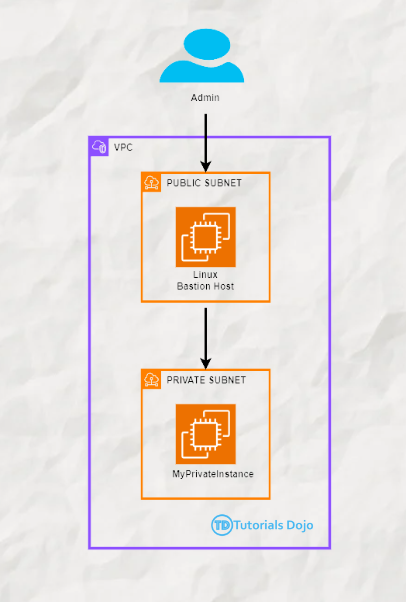
This short article will discuss what a bastion host is and its importance in your cloud architecture. We will also talk about its various use cases, relevance, and the related processes of setting it up in the AWS Cloud. A Bastion host, often called a jump server, is critical to securing cloud environments. It acts as an intermediary providing secure access to resources in a private subnet without exposing them directly to the internet. This setup is essential for maintaining a robust security posture, especially in environments where sensitive data and resources reside within private subnets. In a typical AWS architecture, private instances (those without direct internet access) host sensitive applications and data. However, administrators still need to manage and maintain these instances. Exposing them directly to the internet would be a significant security risk, so a Bastion host is used instead. A Bastion host is a secure access point, allowing administrators to connect to private instances via SSH or RDP, depending on the operating system. Restricting access to the Bastion host alone and using it as a gateway minimizes the attack surface, and your private instances remain shielded from direct exposure. While Bastion hosts remain widely used in traditional environments, more modern alternatives have emerged that offer enhanced security and convenience. For instance, AWS Systems Manager Session Manager allows secure access to EC2 instances without needing a Bastion host or SSH keys, eliminating the need for open inbound ports. Zero Trust networking models and VPC endpoints also provide secure access to resources without the exposure risks associated with a publicly accessible Bastion host. However, Bastion hosts are still relevant, particularly for environments where legacy systems are in use or where modern alternatives are not feasible. They continue to be a key part of many cloud security strategies, especially for organizations that require a simple yet effective solution for secure remote access. The Bastion host is placed in a public subnet within your VPC, meaning it has a public IP address and can be accessed via the Internet. The private instances remain in a private subnet with no direct access to the internet. The Bastion host acts as a middleman—administrators first connect to the Bastion host and then use it to connect to the private instances via SSH. Key points about Bastion hosts: Now that we understand the importance of a Bastion host let’s walk through setting one up in AWS. Take note that the following steps are a simplified and practical example. To create a Bastion host, you’ll launch an EC2 instance in your public subnet. Follow these steps: Navigate to the EC2 Dashboard: In the AWS Management Console, go to the EC2 dashboard. Launch an EC2 Instance: Security Group Configuration: Review and Launch: Review your settings and launch the instance. Once the instance is launched, note the public IP address, as you’ll use it to connect to the Bastion host. Next, you’ll launch another EC2 instance, but this time in the private subnet, which the Bastion host will access. Launch another EC2 Instance: Security Group Configuration: Review and Launch: Review your settings and launch the instance. Once both instances are running, you can access the private instance securely through the Bastion host. Here’s how: Connect to the Bastion Host: Transfer the Private Key: SSH into the Private Instance: If successful, you’ll be connected to the private instance via the Bastion host, ensuring secure and controlled access. By following this guide, you have successfully set up a Bastion host in AWS and used it to access a private instance securely. This setup is critical to maintaining a secure cloud environment, particularly for sensitive workloads. Bastion hosts act as gatekeepers, allowing access to private instances while shielding them from the internet. This strategy is vital for any organization looking to enhance its security posture on AWS. Remember to periodically review and update security groups and configurations to ensure they align with your security policies and best practices. https://aws.amazon.com/solutions/implementations/linux-bastion/
What is a Bastion Host?
Why Use a Bastion Host?
Is a Bastion Host Still Relevant Today?
How Does a Bastion Host Work?
Setting Up a Bastion Host in AWS
Launch a Bastion Host in the Public Subnet
Launch a Private Instance in the Private Subnet
Accessing the Private Instance via the Bastion Host
ssh -i MyKeyPair.pem ec2-user@<BastionHost-Public-IP>
scp -i MyKeyPair.pem MyKeyPair.pem ec2-user@<BastionHost-Public-IP>:/home/ec2-user
chmod 400 MyKeyPair.pem
ssh -i MyKeyPair.pem ec2-user@<PrivateInstance-Private-IP>
Conclusion
Reference:
Understanding the Importance of Bastion Hosts in AWS
AWS, Azure, and GCP Certifications are consistently among the top-paying IT certifications in the world, considering that most companies have now shifted to the cloud. Earn over $150,000 per year with an AWS, Azure, or GCP certification!
Follow us on LinkedIn, YouTube, Facebook, or join our Slack study group. More importantly, answer as many practice exams as you can to help increase your chances of passing your certification exams on your first try!
View Our AWS, Azure, and GCP Exam Reviewers Check out our FREE coursesOur Community
~98%
passing rate
Around 95-98% of our students pass the AWS Certification exams after training with our courses.
200k+
students
Over 200k enrollees choose Tutorials Dojo in preparing for their AWS Certification exams.
~4.8
ratings
Our courses are highly rated by our enrollees from all over the world.