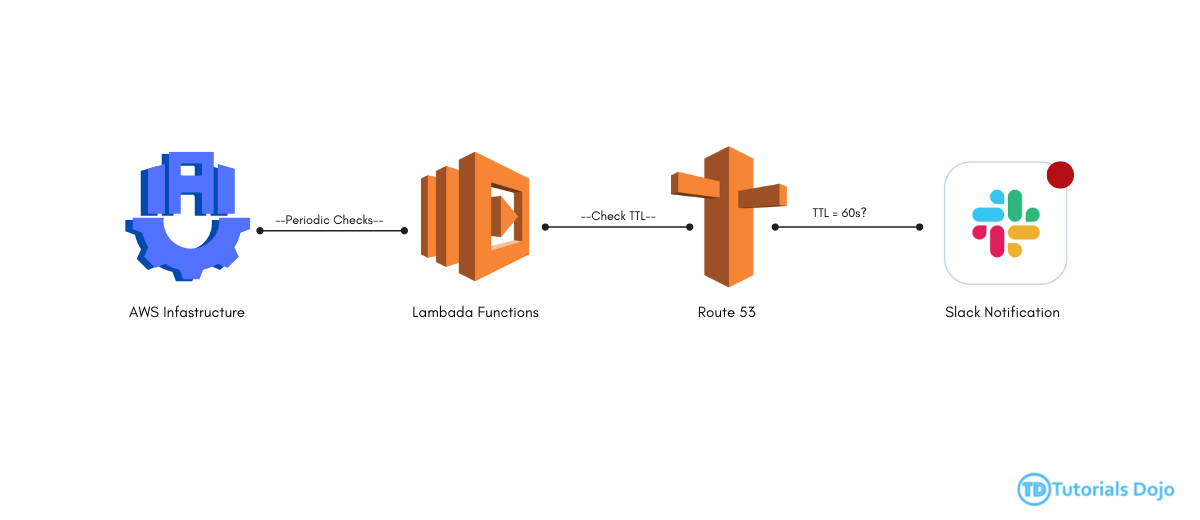
Automating a Slack notification system for Route 53 with a 60-second TTL is intended to provide real-time alerts about DNS records with short TTLs. This setup ensures administrators receive quick notifications via Slack, enabling them to promptly identify and resolve potential issues. Through this proactive measure, the optimal performance and reliability of the AWS infrastructure are maintained. Moreover, this approach allows administrators to avoid potential problems by taking corrective actions promptly and minimizing any potential disruptions to services. Additionally, real-time alerts enable administrators to keep a close watch on DNS configurations, ensuring smooth operation and consistent performance of the AWS infrastructure for end-users. Implementing this solution brings multiple advantages. First, it improves proactive monitoring of Route 53 hosted zones, allowing administrators to quickly identify and address changes in DNS record TTL. This leads to faster troubleshooting and resolution of potential issues, reducing downtime and enhancing service availability. Additionally, utilizing Slack notifications promotes effective communication and collaboration among team members, creating a more unified and responsive operational environment. – In IAM Roles, click add permission → create inline policy. To verify the functionality of the Slack notification system: Implementing a Slack notification system for Route 53 TTL of 60 enhances AWS monitoring capabilities, enabling administrators to promptly identify and respond to DNS record changes. By leveraging proactive alerts and efficient communication channels, this solution contributes to maintaining the stability, reliability, and performance of AWS infrastructure, ultimately ensuring seamless service delivery and user satisfaction. This proactive approach empowers administrators to stay informed about DNS record changes in real-time, allowing them to address any anomalies swiftly and prevent potential service disruptions. Moreover, by utilizing Slack as a communication platform, administrators can collaborate effectively, facilitating quicker resolution of issues and minimizing downtime. Overall, the implementation of this notification system enhances the overall operational efficiency and effectiveness of AWS infrastructure management, resulting in improved service reliability and heightened user satisfaction.
Implementation Steps
– Develop Python scripts for Lambda functions.
– Configure Lambda function settings, including runtime and execution role.
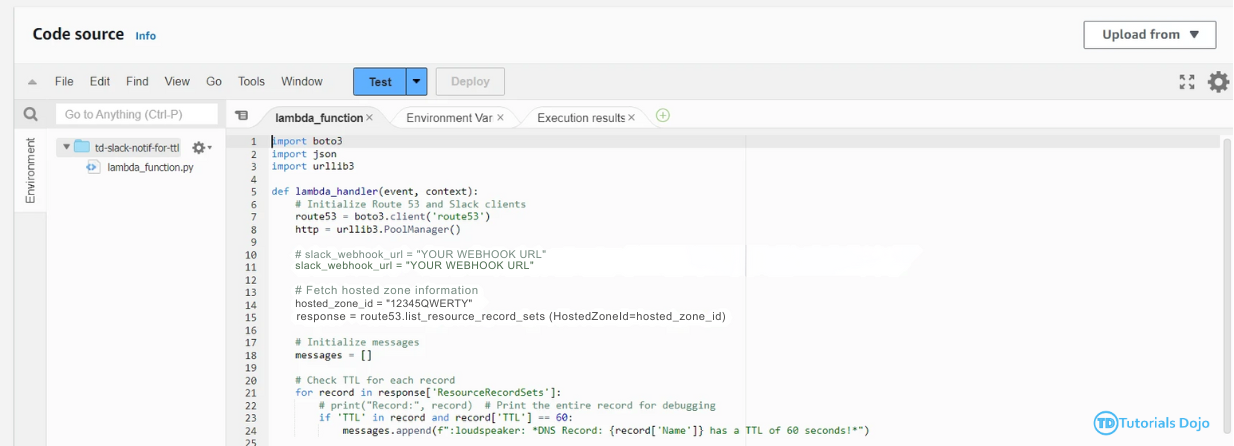
– Paste these codes to the Lambda Function > click Deploy
import boto3
import json
import urllib3
def lambda_handler(event, context):
# Initialize Route 53 and Slack clients
route53 = boto3.client('route53')
http = urllib3.PoolManager()
# slack_webhook_url = "YOUR SLACK WEBHOOK URL"
slack_webhook_url = "YOUR SLACK WEBHOOK URL"
# Fetch hosted zone information
hosted_zone_id = "12345QWERTY"
response = route53.list_resource_record_sets(HostedZoneId=hosted_zone_id)
# Initialize messages
messages = []
# Check TTL for each record
for record in response['ResourceRecordSets']:
if 'TTL' in record and record['TTL'] == 60:
messages.append(f":loudspeaker: *DNS Record: {record['Name']} has a TTL of 60 seconds!*")
if messages:
message_block = {
"type": "section",
"text": {
"type": "mrkdwn",
"text": "\n".join(messages)
}
}
payload = {
"blocks": [message_block]
}
encoded_payload = json.dumps(payload).encode('utf-8') # Encode the payload as bytes
headers = {
"Content-Type": "application/json"
}
response = http.request('POST', slack_webhook_url, body=encoded_payload, headers=headers)
print(response.data.decode('utf-8')) # Print Slack API response for debugging
return {
'statusCode': 200,
'body': json.dumps('Function executed successfully')
}
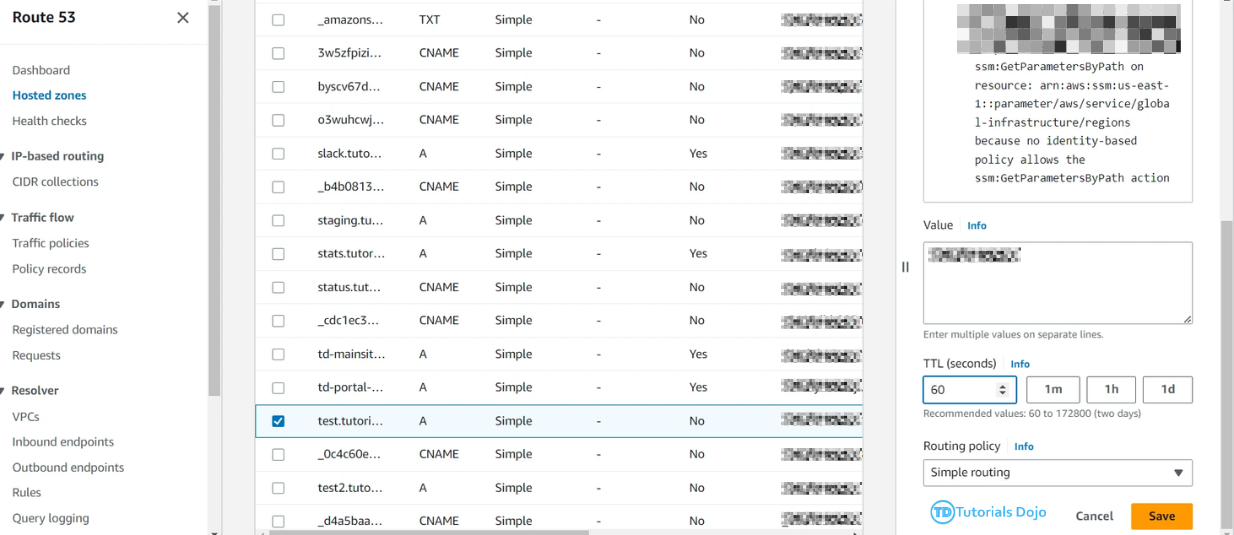
– Set up EventBridge rules to monitor Route 53 hosted zones for TTL changes.
– Under Configuration → Triggers → Create EventBridge to check and monitor if there’s a TTL of 60 seconds in tutorialsdojo Hosted zone daily.
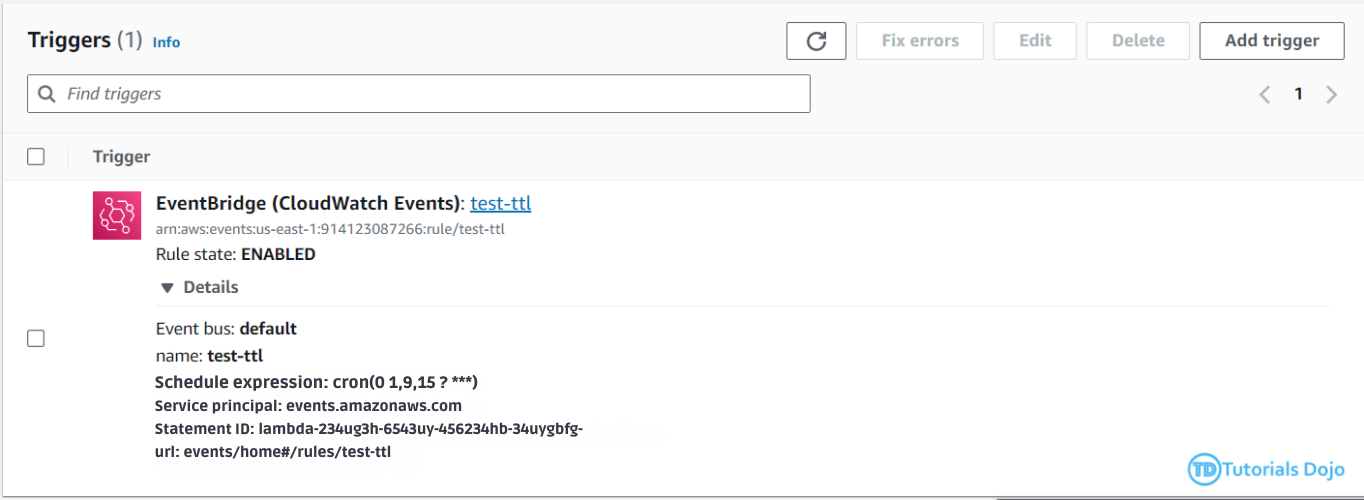
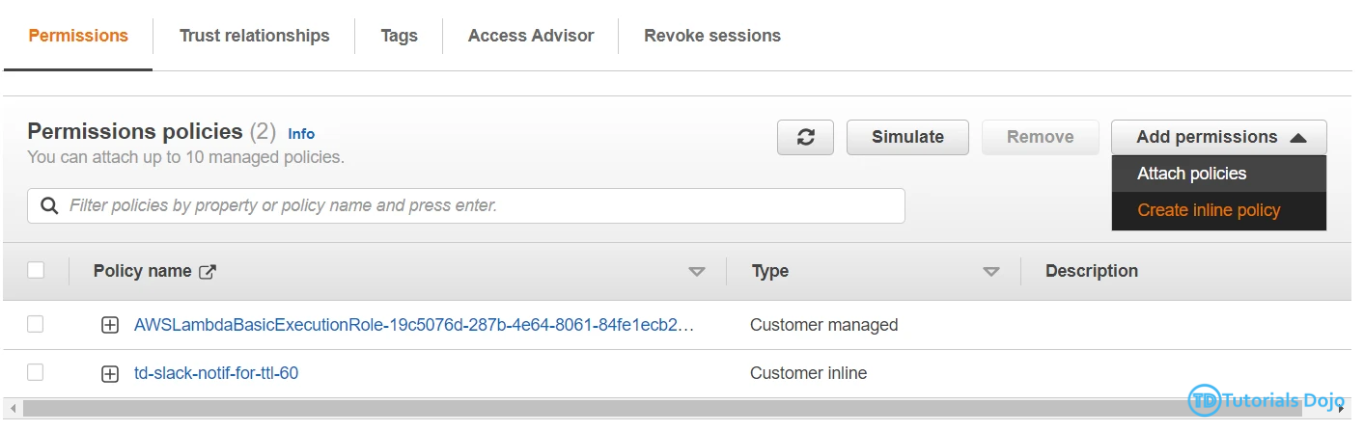
– Next is to add permission to list all the resource record sets in route 53. To do this, go to the Permissions under the Trigger tab. Click the execution role name, and you’ll be redirected to IAM Roles.
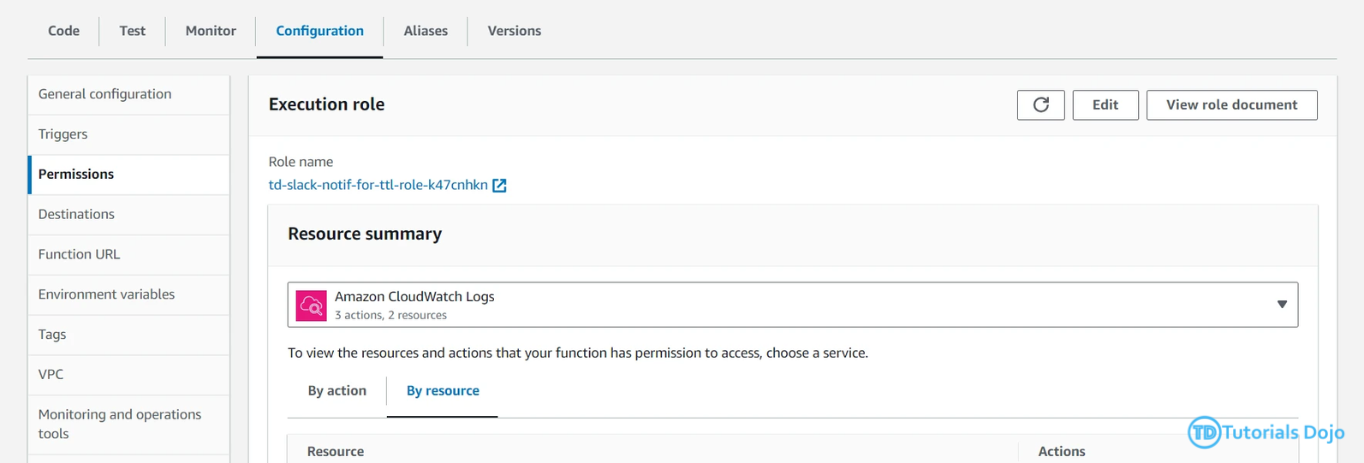
– In the policy editor, switch to JSON and paste this code. After pasting the code, click next, provide the role name, and click the Create Policy button.{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"route53:ListResourceRecordSets"
],
"Resource": "arn:aws:route53:::hostedzone/12345QWERTY"
}
]
}
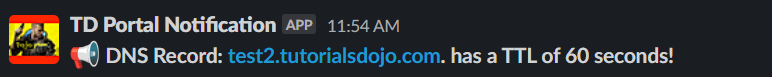
Verification
Conclusion
Automating Slack Notification for Route 53 TTL Changes
AWS, Azure, and GCP Certifications are consistently among the top-paying IT certifications in the world, considering that most companies have now shifted to the cloud. Earn over $150,000 per year with an AWS, Azure, or GCP certification!
Follow us on LinkedIn, YouTube, Facebook, or join our Slack study group. More importantly, answer as many practice exams as you can to help increase your chances of passing your certification exams on your first try!
View Our AWS, Azure, and GCP Exam Reviewers Check out our FREE coursesOur Community
~98%
passing rate
Around 95-98% of our students pass the AWS Certification exams after training with our courses.
200k+
students
Over 200k enrollees choose Tutorials Dojo in preparing for their AWS Certification exams.
~4.8
ratings
Our courses are highly rated by our enrollees from all over the world.