Last updated on January 5, 2026
Microsoft Defender for Identity Cheat Sheet
- Enables you to identify, detect, and investigate advanced threats in your organization.
- Allows you to monitor user activities and information.
- Requires a Microsoft 365 E5, E5 Security, or a standalone Defender for Identity license for deployment.
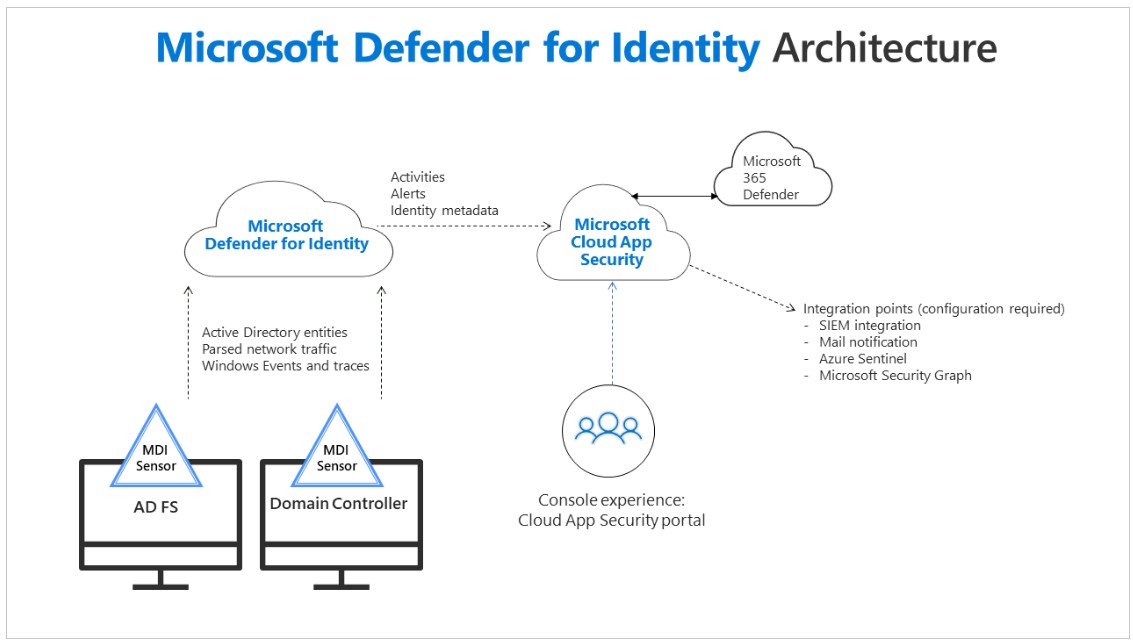
- Uses a light-weight sensor installed on Domain Controllers to analyze network traffic and authentication events.S
- Integrates alerts and data into the unified Microsoft 365 Defender portal for a centralized security view.
- Identify and investigate advanced threats throughout the entire cyber-attack kill chain:
- Reconnaissance – identify attempts by attackers to gain information.
- Compromised credentials – any attempts that compromise user credentials shall be detected.
- Lateral movements – attacks to gain access to sensitive accounts.
- Domain dominance – the attacker has the credentials to access your domain controller. This includes detection of attacks that steal and abuse certificates from Active Directory Certificate Services (AD CS).
- Exfiltration – unauthorized data transfer.
-
Provides automated investigation of alerts and maps lateral movement paths between users and critical assets based on Active Directory permissions.
Microsoft Defender for Identity Cheat Sheet References:
https://www.microsoft.com/en-ww/security/business/threat-protection/identity-defender
https://docs.microsoft.com/en-us/defender-for-identity/what-is