Introduction
In today’s digital era, the importance of security in machine learning (ML) pipelines cannot be overstated. As ML systems increasingly become integral to business operations and decision-making, ensuring the integrity and security of these systems is paramount. A breach or a flaw in an ML pipeline can lead to compromised data, erroneous decision-making, and potentially catastrophic consequences for businesses and individuals alike. This section will delve into why securing ML pipelines is crucial, highlighting the potential risks and impacts of security lapses.
Short Introduction to Amazon SageMaker
Amazon SageMaker is a fully managed service that provides every developer and data scientist with the ability to build, train, and deploy machine learning models quickly. SageMaker removes the heavy lifting from each step of the machine-learning process, making it easier to develop high-quality models. This section will provide an overview of Amazon SageMaker, focusing on its features that simplify the creation and deployment of ML models, with a special emphasis on its security-oriented capabilities.
Learn more: https://docs.aws.amazon.com/sagemaker/
Purpose and Scope
The purpose of this blog post is to guide readers, particularly those at a beginner to intermediate level, through the best practices for securing machine learning pipelines in Amazon SageMaker. We aim to provide a comprehensive understanding of the potential security threats and the effective measures that can be employed to mitigate them. The scope of this post will cover various aspects of security in the context of SageMaker, from data encryption and access control to advanced security techniques. By the end of this article, readers should feel more confident in their ability to secure their ML pipelines within the Amazon SageMaker environment.
Understanding the Security Risks
Potential Security Threats in Machine Learning Pipelines
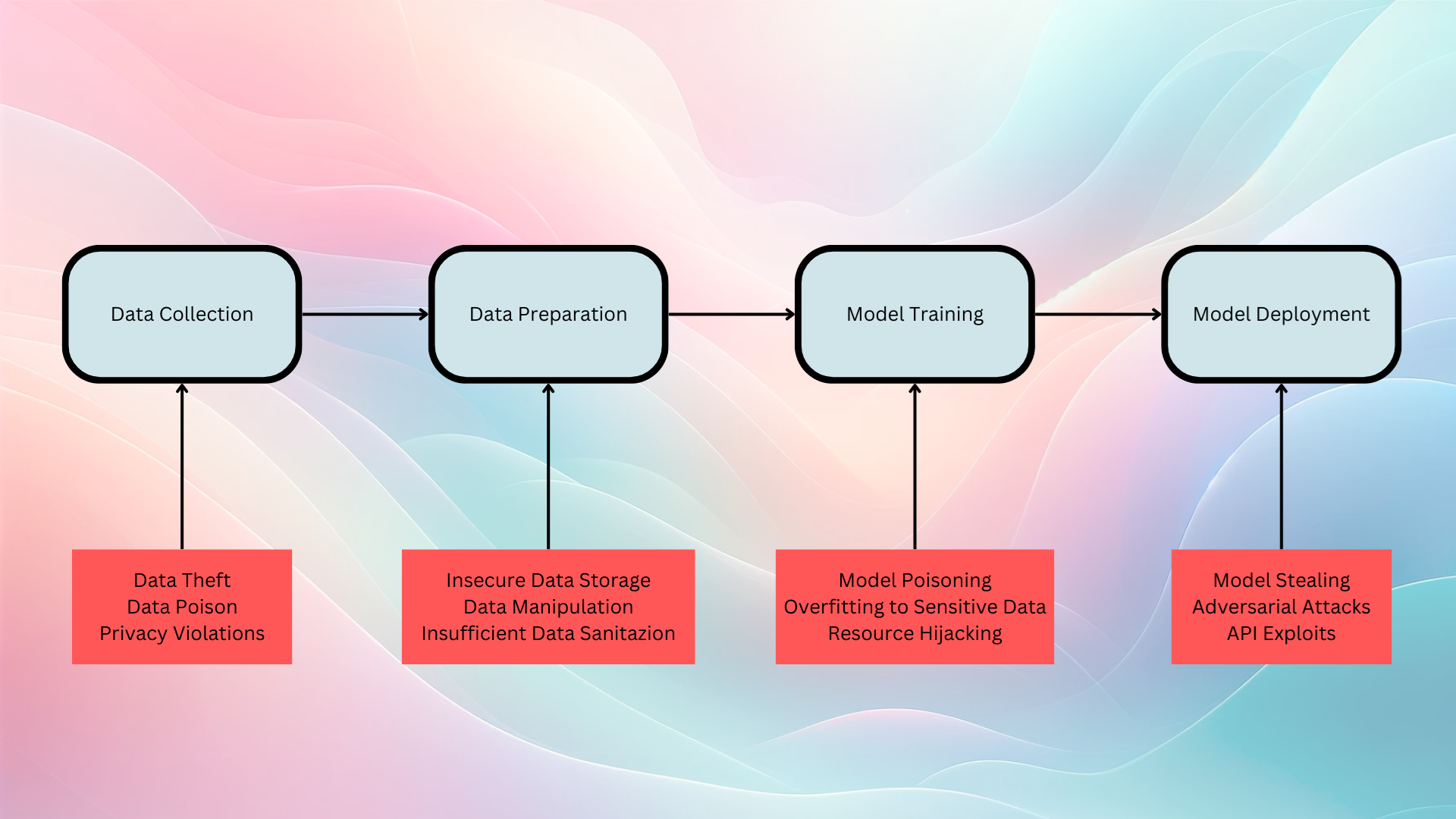
Machine learning pipelines, from data collection to model deployment, face a variety of security threats. Understanding these threats at each stage is crucial for implementing robust security measures.
Data Collection
- Privacy Violations: Collecting data without proper consent or in violation of regulations like GDPR can lead to serious legal and ethical issues.
- Data Poisoning: The intentional insertion of misleading data can skew model outcomes, leading to unreliable or biased predictions.
- Data Theft: Unauthorized access to collected data can compromise confidentiality and integrity.
Data Processing
- Insecure Data Storage: Storing data in unsecured databases can lead to breaches, compromising data integrity.
- Data Manipulation: The alteration of data, either by external attackers or insider threats, can corrupt the model training process.
- Insufficient Data Sanitization: Not properly anonymizing data can lead to privacy risks and unintentional leakage of sensitive information.
Model Training
- Model Poisoning: Introducing biased data during training can manipulate the model’s decision-making.
- Overfitting to Sensitive Data: Models that inadvertently learn and reproduce sensitive information can lead to privacy breaches.
- Resource Hijacking: The misuse of model training infrastructure for other purposes, like crypto mining, can compromise resources and data.
Model Deployment
- Model Stealing: Unauthorized duplication of the machine learning model, often through repeated querying (model extraction attacks).
- Adversarial Attacks: Presenting carefully crafted inputs to the model to cause it to make errors or reveal sensitive information.
- API Exploits: If the model is deployed as a service, its API may be vulnerable to various attacks, including denial of service or unauthorized access.
Unique Risks Associated with Cloud-Based ML Environments
Cloud-based machine learning environments like Amazon SageMaker have revolutionized the field by providing scalable, flexible, and efficient platforms for developing and deploying ML models. However, these environments also introduce unique security challenges that need careful consideration:
- Multi-Tenancy Risks: Cloud environments often operate on a multi-tenant model, where resources are shared among different users. This setup can increase the risk of data leakage or cross-tenant attacks if the isolation mechanisms are not robust enough.
- Increased Attack Surface: The cloud’s accessibility, while a boon for collaboration and efficiency, also expands the attack surface. The APIs and interfaces that enable remote access and control of cloud resources can be potential points of exploitation if not properly secured.
- Dependency on Cloud Service Provider (CSP) Security: In a cloud-based environment, a significant portion of security responsibility is with the CSP. Any vulnerabilities in the CSP’s infrastructure or lapses in their security protocols can directly impact the security of the ML pipelines hosted on their platforms.
- Data Transit Risks: Data frequently needs to be transferred between on-premises systems and the cloud environment. This data in transit is vulnerable to interception, requiring strong encryption protocols to ensure confidentiality and integrity.
- Compliance and Legal Challenges: Ensuring compliance with various data protection and privacy laws (like GDPR, HIPAA) becomes more complex in a cloud environment, especially when data is stored across different regions with varying legal requirements.
- Automated Scaling Vulnerabilities: Cloud environments often provide automated scaling features to handle varying workloads. While beneficial for performance and cost, this can introduce security vulnerabilities as rapid scaling might bypass normal security checks or overwhelm existing security measures.
- Insider Threats: The ease of access to cloud environments also increases the risk of insider threats. Malicious or negligent actions by authorized users can lead to significant security breaches.
Addressing these unique risks requires a combination of robust cloud-specific security measures, vigilant monitoring, and adherence to best practices in cloud security. This makes it essential for ML practitioners to be well-versed not only in ML technologies but also in cloud security principles.
Overview of Security Features in SageMaker
Amazon SageMaker, a comprehensive service by Amazon Web Services (AWS), offers robust features for building, training, and deploying machine learning models at scale. A critical aspect of SageMaker is its focus on security, ensuring that data scientists and ML practitioners can work in a secure and compliant environment. This section explores the various security features, compliance standards, and data protection mechanisms that SageMaker provides.
Built-in Security Features of Amazon SageMaker
- Encryption: SageMaker provides encryption for data at rest and in transit. Data at rest is encrypted using keys managed through AWS Key Management Service (KMS), ensuring data security even when stored. For data in transit, SageMaker employs SSL/TLS encryption to protect data as it moves between AWS services.
- Identity and Access Management (IAM): SageMaker leverages AWS IAM to control access to ML resources. IAM roles and policies enable fine-grained access controls, allowing users to specify who can access what resources and operations.
- Network Isolation: SageMaker offers options to run training jobs and deploy models in an isolated network environment (Amazon Virtual Private Cloud – VPC), reducing exposure to potential external threats.
- Secure Endpoints: When deploying models, SageMaker allows the creation of secure HTTPS endpoints for inference, which are protected by SSL/TLS encryption.
- Logging and Monitoring: Integration with AWS CloudTrail and Amazon CloudWatch enables logging and monitoring of SageMaker operations. This helps in tracking usage and detecting unusual activities that could indicate security threats.
Compliance Certifications and Standards Support
SageMaker is compliant with a variety of international and industry-specific standards, ensuring adherence to stringent security and privacy requirements. This includes:
- ISO Certifications: Including ISO 27001 for information security management and ISO 27017 for cloud security.
- SOC Reports: Service Organization Control reports (SOC 1, 2, and 3) which attest to the security and privacy controls in place.
- GDPR Compliance: Ensuring that data processing aligns with the General Data Protection Regulation requirements, critical for businesses operating in or dealing with the European Union.
How SageMaker Secures Data and Models
SageMaker employs multiple layers of security to protect both data and ML models:
- Model Artefact Encryption: Model artifacts are encrypted, ensuring that they are secure at rest.
- Data Protection: SageMaker provides functionalities to ensure that the data used for training and inference is protected and handled securely, aligning with compliance requirements.
- Security in the ML Lifecycle: From data preprocessing to model training and deployment, SageMaker implements security measures at every stage of the ML lifecycle.
Secure your ML Pipelines in SageMaker
Securing machine learning pipelines in Amazon SageMaker is not just about utilizing its built-in security features; it also involves adhering to best practices that enhance overall security. This section provides actionable guidelines to fortify your ML pipelines against potential threats.
Data Encryption
1. At-rest and In-transit Encryption Methods
- At-rest: Use AWS KMS for managing encryption keys to encrypt data stored in S3 buckets and other storage services used by SageMaker.
- In-transit: Ensure that data transferred between your services and SageMaker is encrypted using SSL/TLS protocols.
2. Key Management Best Practices
- Regularly rotate encryption keys.
- Use customer-managed keys for greater control.
- Implement least privilege access policies for key management.
Access Control
1. Secure Network Configuration
- Use security groups and network access control lists (ACLs) to regulate traffic to and from SageMaker resources.
2. Using Virtual Private Cloud (VPC) and Endpoints
- Deploy SageMaker resources within a VPC for enhanced network isolation.
- Utilize VPC endpoints to securely connect to other AWS services.
Monitoring and Logging
1. Continuous Monitoring Strategies
- Implement continuous monitoring using Amazon CloudWatch to track SageMaker’s operational metrics and logs.
2. Log Management and Anomaly Detection
- Enable logging with AWS CloudTrail to audit SageMaker API calls.
- Use tools like Amazon GuardDuty to detect unusual activities and potential threats.
More Advanced Security Techniques
- Protect SageMaker endpoints with AWS WAF (Web Application Firewall) and security groups to prevent unauthorized access and attacks.
- Leverage machine learning models to analyze patterns and detect anomalies in network traffic and access logs.
- Conduct periodic security audits to assess the effectiveness of existing security measures.
- Stay updated with compliance requirements and ensure that SageMaker deployments adhere to these standards.
Adopting these best practices will significantly enhance the security of your ML pipelines in Amazon SageMaker, ensuring a more robust and secure environment for your ML projects.
Conclusion
In this article, we traversed the landscape of securing machine learning pipelines in Amazon SageMaker. We started by understanding the various security risks in machine learning pipelines, particularly focusing on each stage of the ML lifecycle, from data collection to deployment. We then delved into the specific security features of Amazon SageMaker, highlighting how it caters to the need for robust security in ML operations.
Following this, we discussed best practices for enhancing security in SageMaker, covering crucial aspects like data encryption, access control, network security, and continuous monitoring. We also touched upon advanced security techniques, including the use of AI for threat detection and the importance of regular security audits.
Ongoing Importance of Security in ML Pipelines
The importance of security in ML pipelines cannot be overstated. As technology evolves and the use of machine learning becomes more pervasive, the potential for security breaches also increases. The consequences of such breaches can be far-reaching, affecting not just the integrity of ML models but also the privacy and safety of individuals and organizations. Therefore, maintaining a vigilant and proactive approach to security is essential.
Final Thoughts and Recommendations
Securing your ML pipelines, especially in cloud-based environments like Amazon SageMaker, requires a continuous commitment to following best practices, staying informed about emerging threats, and adapting to new security technologies. It is a combination of utilizing the right tools, adhering to best practices, and fostering a culture of security awareness within your team.
Remember, security in machine learning is not just a one-time setup but a dynamic, ongoing process. As you continue to develop and deploy ML models, keep security at the forefront of your operations. By doing so, you can not only protect your models and data but also build trust with your users and stakeholders.
Resources:
https://docs.aws.amazon.com/sagemaker/latest/dg/best-practices.html
https://docs.aws.amazon.com/sagemaker/latest/dg/best-practice-endpoint-security.html
https://aws.amazon.com/blogs/security/secure-deployment-of-amazon-sagemaker-resources/