Last updated on May 2, 2023
AWS Config allows you to set “rules” to evaluate configuration settings on your AWS resources. The result of these rule evaluations are then displayed on the AWS Config web console. You can control the frequency of rule evaluations by AWS Config by specifying a trigger. A trigger refers to the method of evaluation for your config rules. There are two types of triggers to select from when creating a rule.
1. Configuration Changes
When “configuration changes” is enabled, AWS Config will evaluate the config rule when specific resources are created, changed, or deleted. In simple terms, as the name implies, AWS Config will start evaluating the rule whenever it detects a change in configuration to the resources you are checking compliance to, whether it’s an EC2 or ALB, or any resource that you defined.
You can set the rule’s scope to identify which resources trigger the evaluation. The rule scope can include the following:
- One or more resource types
- A combination of a resource type and a resource ID
- A combination of a tag key and value
- When any recorded resource is created, updated, or deleted
Use Case
Enable configuration changes when you want a sense of urgency on your compliance to the internal guidelines of your company.
For example, your development team should use only t2.micro instance type for their activities. There’s a strict rule in your company to reprimand anyone who launches a different instance type. As the Systems Administrator, you want to get notified right away whenever a violation happens. This type of situation is a good use case for configuration changes.
2. Periodic
When “periodic” is enabled, AWS Config will evaluate the config rule at a frequency that you choose (e.g. 1 hour, 12 hours, 24 hours). So as opposed to configuration changes, this type of trigger is not event-driven.
Use Case
Enable Periodic when you’re okay with less strict compliance in terms of urgency. Use this if you want to schedule the evaluation of config rule at a certain interval.
For example, as the Systems Administrator, you want to ensure that multi-factor authentication (MFA) is enabled for new and current IAM users. To check for compliance, you added the AWS Config managed rule, iam-user-mfa-enabled, on your AWS Organization. You don’t want to get notified right away whenever there’s a violation of compliance. Instead, you would rather deal with it at a 24-hour interval. So you enabled periodic and set the frequency to 24 hours.
With AWS Config, you pay $0.003 per configuration item recorded in your AWS account per AWS Region. It also charges you with $0.001 per rule evaluation per region (for the first 100,000 rule evaluations). So if you know that your AWS account will have a lot of changes throughout the day, it will be cheaper to have a Periodic trigger (since it will run just once a day) instead of an “event-driven” configuration changes trigger (which will run on every event).
Getting Started On Trigger types:
1. Go to AWS Config Dashboard
2. On the left-most pane, click “Rules” then click “Add rule”
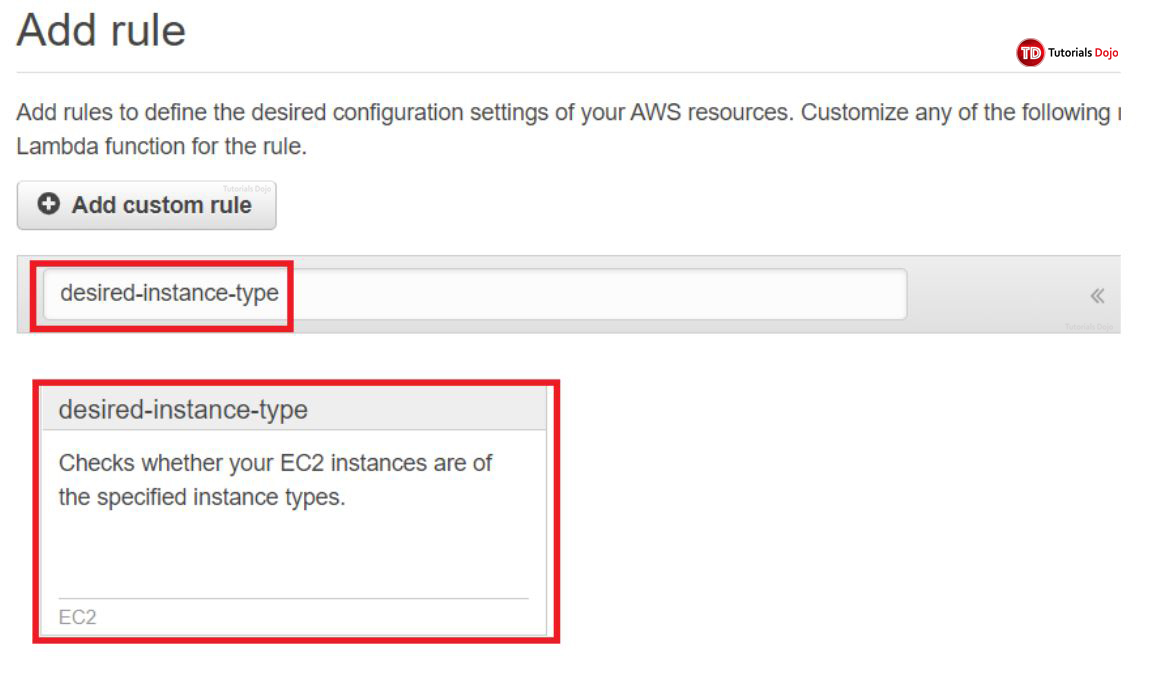
We’ll look into a managed config rule “desired-instance-type”.
3. Type “desired-instance-type” on the space provided. Click the card to proceed.
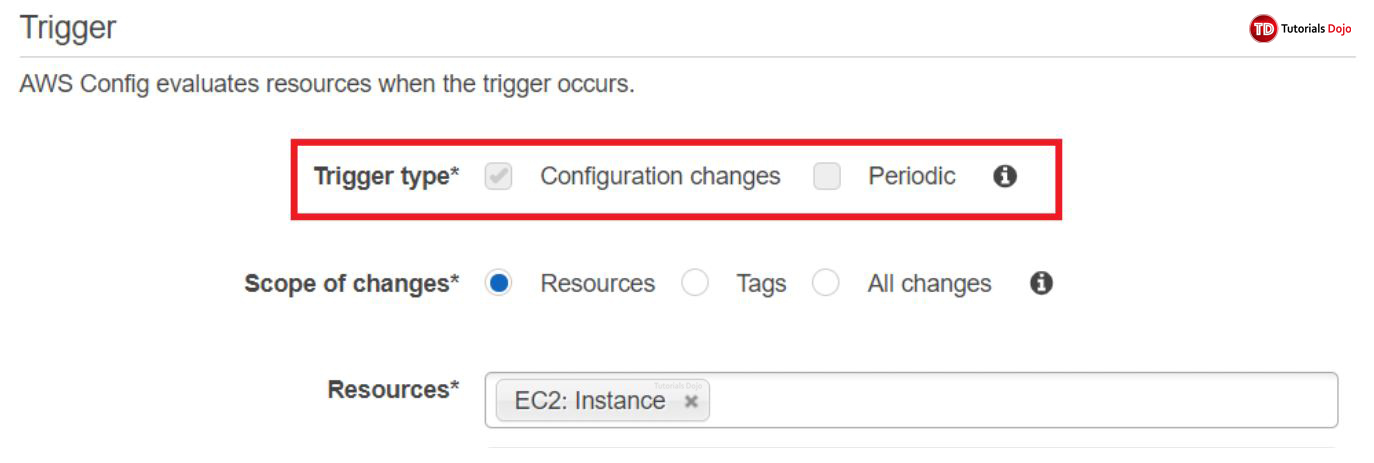
4. Scroll down until you find “Trigger”.
5. Choose a trigger type. Note that in a managed config rule, the trigger type is automatically defined for you and you cannot modify it. However, you’re free to change it however you want when you add a custom rule.
Reference:
https://docs.aws.amazon.com/config/latest/developerguide/evaluate-config-rules.html