The SC‑200 Security Operations Analyst Associate certification is designed for Security Operations Analysts who leverage tools like Microsoft Sentinel, Microsoft Defender XDR, Microsoft Defender for Cloud, Microsoft Security Copilot, and third-party security solutions. The role focuses on threat monitoring, investigation, response, and threat hunting across cloud and on-premises environments while collaborating with stakeholders to enhance security posture and define organizational security standards.
The exam will measure your skills in the following areas.
- Manage a security operations environment
- Configure protections and detections
- Manage incident response
- Manage security threats
If you are eager to learn more about the SC-200 Microsoft Security Operations Analyst Associate exam, I recommend checking out the official exam skills outline. This study guide contains comprehensive review materials designed to help you pass the exam with confidence.
Study Materials
Prior to attempting the Microsoft Certified: Security Operations Analyst Associate, it is highly advised to go through these study materials. These resources are specifically designed to aid you in grasping the intricate concepts and services that will be addressed in the exam.
- Microsoft Learn – this website offers a variety of learning paths for different Microsoft certifications. For the SC‑200 Security Operations Analyst Associate certification exam, you can focus on the following topics:
- Azure Documentation – the documents provide a comprehensive set of resources, including overviews, tutorials, examples, and how-to guides, which can help you understand various Azure services in depth.
- Azure Blog – to stay up-to-date on the latest technologies and offerings from Microsoft Azure, you can subscribe to their newsletter.
- Azure FAQs – the Azure documentation includes a comprehensive FAQ section that answers common questions about Azure services, use cases, and comparisons.
- Azure Free Account – the Azure portal offers a 12-month trial that gives you hands-on experience with Azure services. You’ll also get free credits to use for the first 30 days.
- Tutorials Dojo’s Azure Cheat Sheets – our cheat sheets make it easy to understand the information found in the Azure documentation. They are presented in a concise bullet-point format that highlights the essential concepts.
- Tutorials Dojo’s SC-200 Microsoft Security Operations Analyst Associate Practice Exams – our practice exams are consistently ranked among the best in the market. Each question comes with comprehensive explanations that will help you understand the crucial concepts you need to succeed in your Microsoft Azure certification exam on your first attempt.
- Azure Security Center Documentation – Essential for understanding threat protection, security posture management, and security alerts.
- Microsoft Security Blog – Stay up to date with the latest security technologies, incidents, and product updates.
- Microsoft Security FAQs – Answers to common questions about the configuration, integration, and use of Microsoft security tools.
Azure Services to Focus On
Azure documentation is the main source of information when preparing for the SC-200 Microsoft Security Operations Analyst Associate certification exam. To understand the scenarios in the exam, make sure you have a solid understanding of the following services:
- Microsoft Entra ID
- Familiarize yourself with securing users and groups, implementing multi-factor authentication (MFA) for access to Azure resources, configuring Conditional Access policies for cloud resources, and managing service principals.
- Emphasize understanding Azure built-in roles, custom roles, and Microsoft Entra roles.
- Role assignment management for Sentinel and Defender.
- Microsoft Sentinel
- Understand workspace architecture, role-based access control, and retention policies.
- Configure data connectors for cloud and on-premises data sources.
- Develop and tune analytics rules, automation rules, and playbooks.
- Conduct threat hunting using KQL, bookmarks, and workbooks.
- Integrate MITRE ATT&CK framework mapping into hunting and detection.
- Microsoft Defender XDR (including Defender for Endpoint, Defender for Office 365, Defender for Identity, Defender for Cloud Apps)
- Configure alert and vulnerability notification rules.
- Set up endpoint detection, automated investigation, and attack disruption.
- Manage device groups, permissions, and exposure scores.
- Investigate and remediate incidents across endpoints, email, identities, and cloud apps.
- Use device timeline, evidence collection, and live response sessions.
- Microsoft Defender for Cloud
- Enhance security posture across Azure, hybrid, and multicloud workloads.
- Understand Secure Score, recommendations, regulatory compliance, and policy assignments.
- Configure workload protections for servers, databases, containers, and storage.
- Respond to security alerts and incidents generated from cloud resources.
- Azure Arc
- Extend Sentinel and Defender coverage to hybrid and multicloud environments.
- Unified security management for on-premises and non-Azure resources.
- Microsoft Security Copilot
- Create and manage promptbooks for standardized investigations.
- Connect to Microsoft and third-party security data sources.
- Generate summaries, guided incident investigations, and remediation suggestions.
- Azure Key Vault
- Gain proficiency in managing secrets, keys, and certificates using Azure Key Vault.
- Learn to configure access policies, implement key rotation, and understand features like soft-delete and retention of deleted objects.
- Azure Monitor
- Explore how to collect, analyze, and respond to telemetry data from both Azure and on-premises environments.
- Focus on monitoring security events and creating alerts for operational and security-related incidents.
- Azure Logic Apps
- Secure Logic App workflows, ensuring safe data processing and integration with other Azure services.
- Learn how to connect with Microsoft Sentinel playbooks to automate incident response.
- Azure Policy
- Implement governance and compliance controls using Azure Policy.
- Assess resource compliance, manage policy definitions, and align configurations with organizational standards.
- Understand how to integrate with Defender for Cloud to apply security recommendations.
- Azure RBAC
- Manage access to Azure resources using built-in and custom roles.
- Apply least-privilege principles to ensure secure and appropriate access across your environment.
- Microsoft Purview
- Manage data governance, data classification, and compliance across environments.
- Integrate Purview with Sentinel for incident response and compliance tracking.
- Monitor and enforce data access policies, insider risks, and data loss prevention (DLP) within organizations.
- Azure Information Protection
- Learn to classify, label, and protect sensitive documents and emails. Configure and enforce data protection policies to safeguard confidential information throughout its lifecycle.
Validate Your Knowledge
If you’re feeling confident because you’ve followed the recommended materials above, it’s time to test your knowledge of various Azure concepts and services. For high-quality practice exams, you can use the Tutorials Dojo SC‑200 Security Operations Analyst Associate Practice Exams.
These practice tests cover the relevant topics that you can expect from the real exam. It also contains different types of questions such as single choice, multiple response, hotspot, yes/no, drag and drop, and case studies. Every question on these practice exams has a detailed explanation and adequate reference links that help you understand why the correct answer is the most suitable solution. After you’ve taken the exams, it will highlight the areas that you need to improve on. Together with our cheat sheets, we’re confident that you’ll be able to pass the exam and have a deeper understanding of how Azure works.
Sample Practice Test Questions:
Question 1
A multinational law firm manages its operations under a Microsoft 365 subscription. The IT department utilizes Microsoft Defender XDR to monitor threats, Microsoft Purview for compliance and data governance, and Exchange Online to manage internal and external email communications.
As part of a regulatory audit, the compliance officer is required to:
-
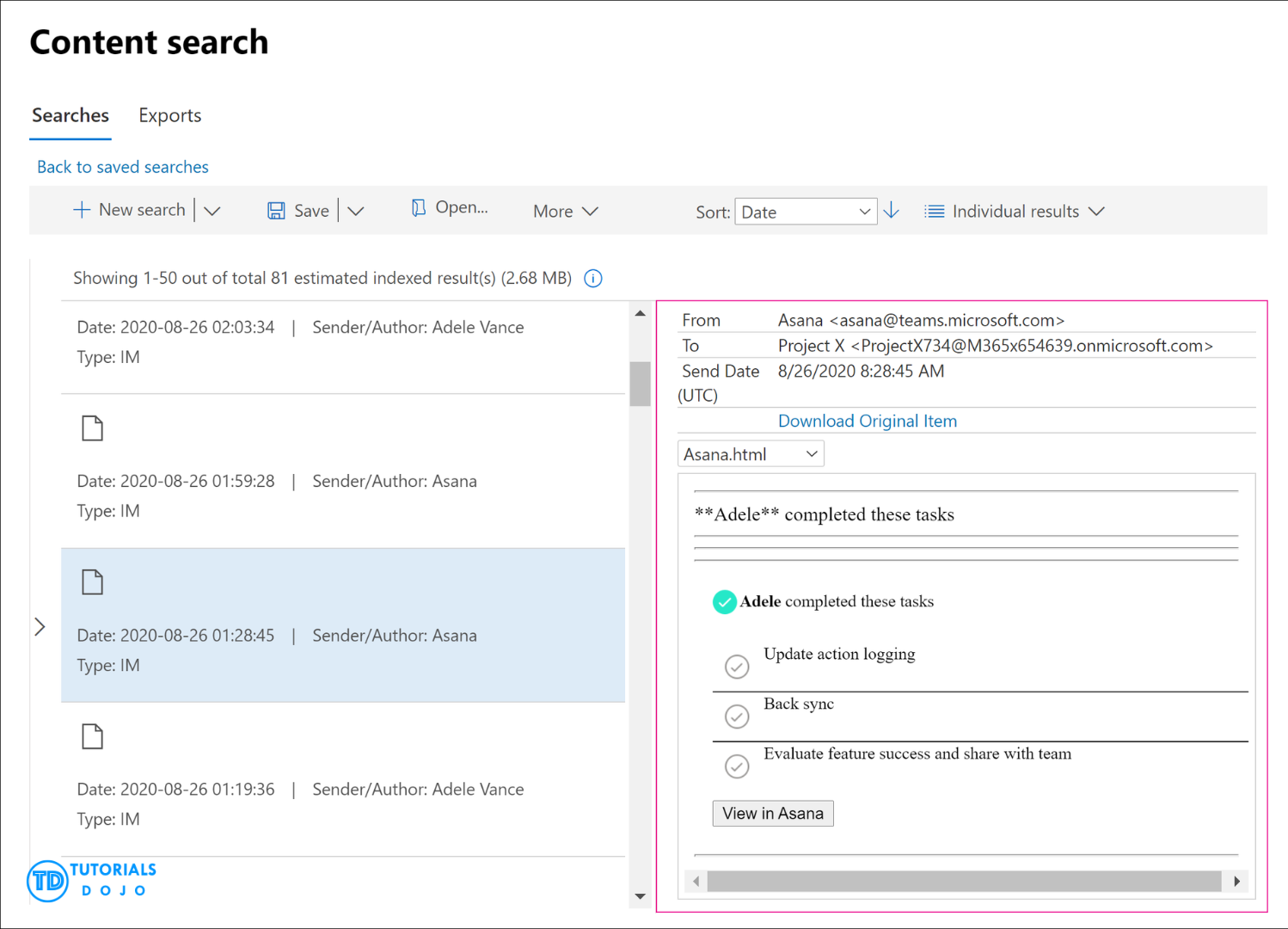
Confirm that no threat indicators are associated with recent communications from Agila Ltd.
-
Search for all emails from Agila Ltd. containing PDF attachments received over the past 30 days.
-
Identify the recipient mailboxes involved.
The solution should require minimal administrative effort and allow email results to be exported for further review.
Which tool best supports the email search and retrieval task in this process?
1. Microsoft Defender XDR incident response
2. Microsoft Purview compliance manager
3. Microsoft Purview content search
4. Microsoft Defender XDR advanced hunting
Question 2
You manage security operations for a global company using an Azure subscription with Microsoft Sentinel, along with Log Analytics for centralized data collection.
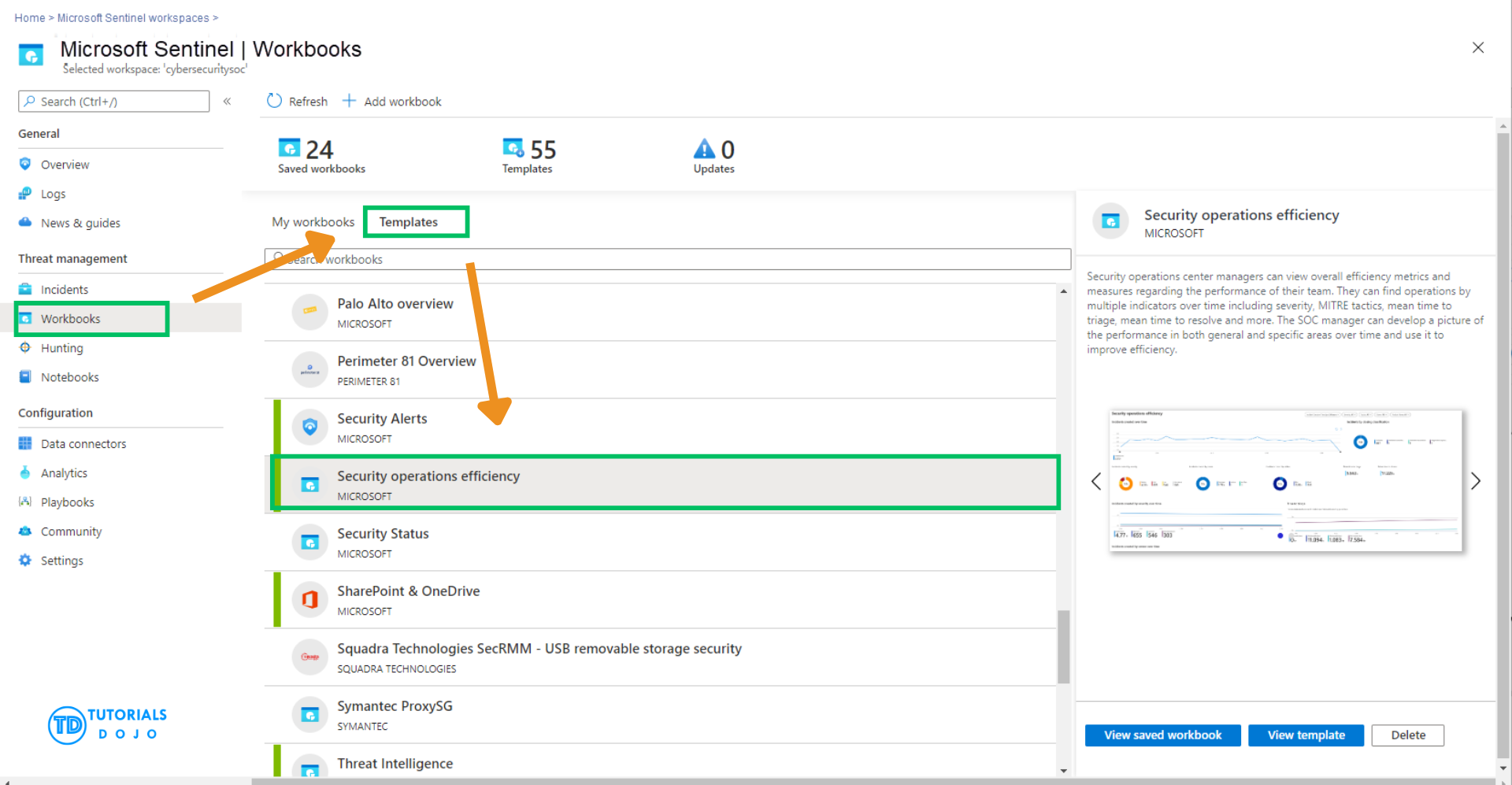
To support an internal audit, you need a custom workbook that shows the average time to triage and close incidents. To save time and reduce effort, you plan to start with a built-in workbook template in Microsoft Sentinel.
Which built-in workbook template in Microsoft Sentinel best meets your requirements?
- Threat Intelligence
- Investigation Insights
- Security Alerts
- Security operations efficiency
For more Azure practice exams questions with detailed explanations, check out the Tutorials Dojo Portal.
Final Remarks
Hands-on experience is as important as understanding the theory behind Azure security. Spend time using the Azure portal to test settings, check security features, and try out threat detection tools. This will help you understand how things work and build your confidence. Make sure you also study key topics like Microsoft Defender, KQL queries, and incident response steps. Learning both the theory and the practical side will help you prepare well for the exam. Azure changes often, so check for updates to services and security features. This will keep your knowledge up to date.
Good luck with your SC-200 Microsoft Security Operations Analyst Associate exam. Your effort and focus will help you succeed.