🤗 Hugging Face: Empowering the Future of AI for Everyone
Artificial Intelligence (AI) has long been seen as a way to create a brighter and more efficient future, but it often seemed limited to large technology companies and top researchers. Recently, platforms like Hugging Face have changed this by making AI tools available to more people. Creators, educators, small business owners, and high school students can now access and use AI technology. Hugging Face functions like GitHub for machine learning, providing valuable tools to [...]
My AWS Certified DevOps Engineer Professional Exam Experience in 2025
Having a certification is more than just a title. For me, it was a way to validate what I’ve been learning and applying over time. It was also a personal challenge—to prove to myself that I could take on one of the toughest AWS certifications, like passing my AWS Certified DevOps Engineer Professional in 2025, and come out stronger on the other side. Earning it boosted my confidence and opened new career opportunities, reinforcing [...]
What Are AI Agents?
Imagine this: You just finished class and told your AI, “Hey, list all my new assignments, check for any upcoming exams, and remind me what topics I still need to study.” Or “These are my upcoming to-dos, can you add them to my calendar so I can keep track?” Imagine the relief of not having to follow up with prompts or micromanage every step. In just a few seconds, your tasks are neatly logged [...]
Creativity-Driven Innovation with Meta Llama 4, Canva Magic Studio and Other Gen AI Tools
Have you ever wondered where you belong in tech? Or how your creativity can be leveraged with technology instead of being pushed aside? That’s where design comes in. Every interface you’ve ever used was made possible because someone saw tech not just as code, but as a canvas. This intersection of design and technology is where creativity-driven innovation with AI is starting to thrive. It’s okay if you haven’t figured it all out yet. [...]
Avoiding Unintended Costs: A Cautionary Guide to Enabling Amazon QuickSight
I still remember the day I first explored Amazon QuickSight on the AWS Console. I was excited, eager to dive into the world of data analytics, and ready to experiment with creating dashboards. Without thinking much, I clicked a few buttons, followed the prompts, and before I knew it, I had enabled QuickSight for my account. What I didn’t realize was that simply enabling the service would lead to an automatic subscription, with charges [...]
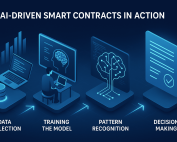
When Contracts Learn: The Power of AI-Driven Smart Contracts in Blockchain
Have you ever clicked "I agree" on a long contract or terms and conditions that pop up when you install a new application—and then forget about it? We know that it is not recommended to do that, but those long blocks of text are just not it. On the other side, writing and reviewing those agreements is just as painful. Anyone who has tried to write a contract knows the struggle of reading [...]
Ramp Up your Mobile Development with FlutterFlow
As a developer, time is one of the most essential factors in developing projects, such as websites, mobile applications, and others. Most projects take much planning, meetings, agenda settings, blah blah blah, before they even reach the development phase. But what if we throw time out of the window? What if a supposed year-long project is already due for the next 3 months? What approach should we use to solve this issue and possibly excel [...]
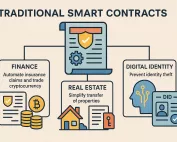
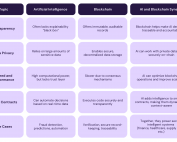
What Makes AI + Blockchain A Promising Synergy
Nowadays, two of the most transformative technologies are on a collision course with the masses: “AI vs. Blockchain?” Keep in mind that these two are entirely different, and they function individually, which gives the two a very dynamic opposition. Yet, it’s precisely those differences that make their fusion a promising breakthrough. There’s really no better player between the two. Seriously, why not go for BOTH, right? Just imagine what these two advancements can [...]
Cloud-9.3: Accessing and Configuring Your Amazon EC2 Instance
Hey, this is Step 3 of our 9-step website portfolio building with AWS! Got lost? Click here to go to the main article, and here for the second step! Now that your EC2 instance is up and running, you might have noticed something strange, every time you stop and start the instance, the public IP address changes. This means the link to your website will keep changing too, which isn’t ideal if you want [...]
AGI vs. ASI vs. ANI: AI Stages Towards Super Intelligence
"You know AI can write poems, drive cars, and even beat humans in chess... but have you ever asked yourself: What kind of AI are we really dealing with? And how close are we to something smarter than us?" Let’s break this down the way I’d explain it to a friend with curiosity, good vibes, and maybe a few deep thoughts that'll have you staring at the ceiling tonight. First things first, what [...]