Last updated on September 1, 2023
Here are 10 AWS Certified Advanced Networking Specialty ANS-C01 practice exam questions to help you gauge your readiness for the actual exam.
Question 1
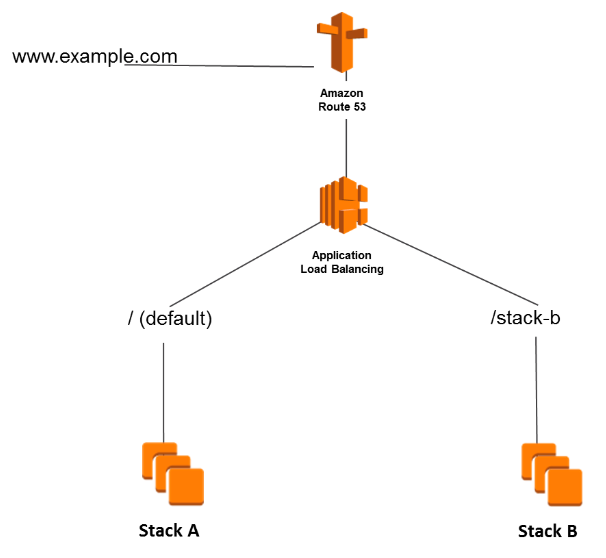
A company is building its customer web portal in multiple EC2 instances behind an Application Load Balancer. The portal must be accessible on www.tutorialsdojo.com as well as on its tutorialsdojo.com root domain.
How should the Network Engineer set up Amazon Route 53 to satisfy this requirement?
- Set up an Alias A Record for tutorialsdojo.com with the ALB as the target. For the www.tutorialsdojo.com subdomain, create a CNAME record that points to the ALB.
- Set up a CNAME Record for tutorialsdojo.com with the ALB as the target. For the www.tutorialsdojo.com subdomain, create a CNAME record that points to the ALB.
- Set up a CNAME Record for tutorialsdojo.com with the ALB as the target. For the www.tutorialsdojo.com subdomain, create an Alias A record that points to the ALB.
- Set up a non-alias A Record for tutorialsdojo.com with the ALB as the target. For the www.tutorialsdojo.com subdomain, create a CNAME record that points to the ALB.
Question 2
A company has a hybrid cloud architecture that connects its on-premises Microsoft Active Directory to its Amazon VPC. The company is launching an application that uses Amazon Elastic MapReduce with a fleet of On-Demand EC2 instances. Two AWS Managed Microsoft AD domain controllers as well as the DHCP options set of the VPC have been provisioned and properly configured. The Network Engineer must ensure that the requests destined for the Route 53 private hosted zone are sent to the VPC-provided DNS.
What should the Engineer implement in order to satisfy this requirement?
- Set up a new conditional forwarder to the Amazon-provided DNS server.
- Configure a seamless EC2 Domain-Join in the AWS Managed Microsoft AD.
- Create a new PTR record in the Route 53 private hosted zone that points to the on-premises Microsoft Active Directory.
- Set up an Amazon Connect omnichannel connection to ensure that the requests destined for the Route 53 private hosted zone are sent to the VPC-provided DNS.
Question 3
A company has a suite of publicly accessible web applications that are hosted in several Amazon EC2 instances. To improve the infrastructure security, the Network Engineer must automate the network configuration analysis of all EC2 instances that regularly checks for ports that are reachable from outside the VPC. This will protect the architecture from malicious activities and port scans by external systems. The solution should also highlight network configurations that allow for potentially malicious access, such as mismanaged security groups, ACLs, IGWs, and other vulnerabilities.
What should the Engineer do to satisfy this requirement?
- Amazon Inspector
- Bidirectional Forwarding Detection (BFD)
- AWS Security Hub
- Amazon Macie
Question 4
The company’s on-premises network has an established AWS Direct Connect connection to its VPC in AWS. A Network Engineer is designing the network infrastructure of a multitier application hosted in an Auto Scaling group of EC2 instances. The application will be accessed by the employees from the on-premises network as well as from the public Internet. The network configuration must automatically update routes in your route table based on your dynamic BGP route advertisement.
What should the Engineer do to implement this network setup?
- Enable route propagation in the route table of the VPC and specify the virtual private gateway as the target.
- Set up two different route tables in the VPC. The first route table must have a default route to the Internet Gateway and the second table has a route to the virtual private gateway.
- Disable the default route propagation option in the route table of the VPC and add a specific route to the on-premises network. Choose the virtual private gateway as the target. Enable the route propagation option in the customer gateway.
- Modify the main route table of the VPC to have two default routes. The first route goes to the public Internet via the Internet Gateway while the second route goes to the on-premises network via the virtual private gateway.
Question 5
An enterprise is extending its on-premises data storage systems using AWS. A Network Engineer established an AWS Direct Connect connection with a Public Virtual Interface (VIF) to the on-premises network to allow low latency access to Amazon S3. The Engineer must ensure that the network connection is properly secured.
Which of the following is a valid security concern about this network architecture?
- AWS Direct Connect advertises all public prefixes with the well-known NO_EXPORT BGP community tag to help control the scope (regional or global) and route preference of traffic. However, the NO_EXPORT BGP community tag is only supported for private virtual interfaces and transit virtual interfaces.
- The prefixes are always advertised to all public AWS Regions so all Direct Connect customers in the same or different region can access your router as long as they also have a Public VIF. You cannot apply BGP community tags on the public prefixes.
- It’s not possible to directly access an S3 bucket through a public virtual interface (VIF) using Direct Connect. You must have a pre-configured VPC endpoint for Amazon S3.
- Prefixes are advertised to all public AWS Regions (global) by default. The Network Engineer must add a BGP community tag to control the scope and route preference of the traffic on public virtual interfaces.
Question 6
A Network Administrator is instructed to support high-throughput processing workloads between the company’s on-premises Storage Gateway appliance and AWS Storage Gateway. She must establish a dedicated network connection to reduce the company’s network costs, increase bandwidth throughput, and provide a more consistent network experience than Internet-based connections.
What are the steps that the Administrator should do to properly implement this integration? (Select THREE.)
- Create and establish an AWS Direct Connect connection between the on-premises data center and the Storage Gateway public endpoints.
- Establish an AWS Managed VPN connection between the on-premises data center and the Storage Gateway private endpoint.
- Connect the on-premises Storage Gateway appliance to the AWS Direct Connect router.
- Connect the on-premises Storage Gateway appliance to the VPC via a Virtual Public Gateway.
Question 7
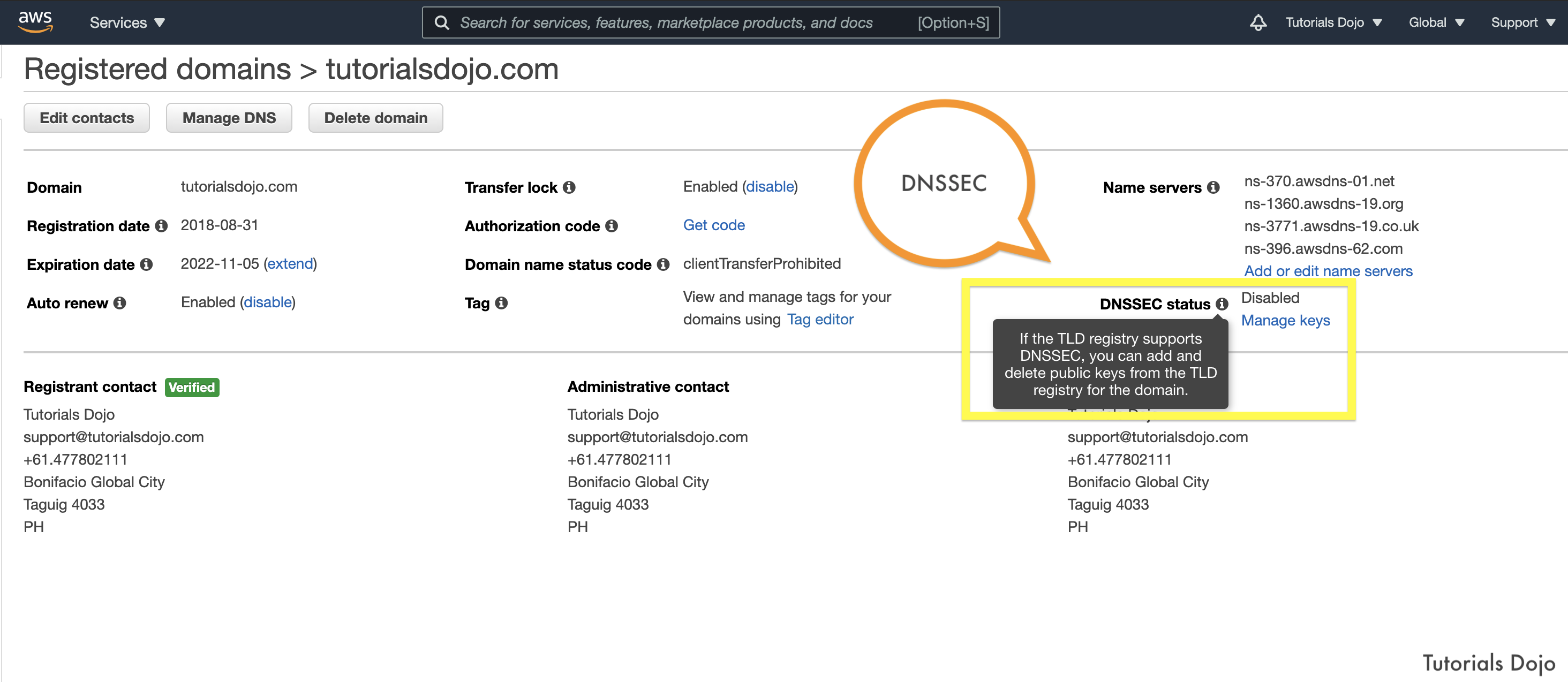
A multinational company has several public websites that were registered using a 3rd-party DNS registrar. The DNS services being used by their websites are from an external service provider, which also includes the Domain Name System Security Extensions (DNSSEC) feature.
The company needs to transfer the domain registration and the DNS services to Amazon Route 53. The migration should have little to no downtime as the websites are already running production workloads.
Which of the following is the most operationally efficient solution with the LEAST amount of downtime?
- Create a new hosted zone and DNS records in Amazon Route 53. Lower the TTL (time to live) setting of the NS (name server) record to 300 and remove the Delegation Signer (DS) record from the parent zone in the current DNS service provider. Lower the TTL setting of the NS record in the Route 53 hosted zone. Once the TTL expires, update the NS records to use Route 53 name servers and monitor the traffic. Increase the TTL to 172800 seconds for the NS record once the migration is complete. Transfer domain registration to Amazon Route 53 and re-enable DNSSEC signing.
- Create a new hosted zone and DNS records in Amazon Route 53 with the DNSSEC feature enabled. Lower the TTL (time to live) setting of the NS (name server) record to 300. Increase the TTL setting of the NS record in the Route 53 hosted zone. Once the TTL expires, update the NS records to use Route 53 name servers and monitor the traffic. Lower the TTL to 600 seconds for the NS record once the migration is complete. Transfer domain registration to Amazon Route 53 and re-enable DNSSEC signing.
- Create a new hosted zone and DNS records in Amazon Route 53. Lower the TTL (time to live) setting of the NS (name server) record to 300 and remove the Delegation Signer (DS) record from the parent zone in the current DNS service provider. Transfer domain registration to Amazon Route 53, where the DNSSEC will be automatically re-enabled. Lower the TTL setting of the NS record in the Route 53 hosted zone. Once the TTL expires, update the NS records to use Route 53 name servers and monitor the traffic. Set the TTL to 600 seconds for the NS record once the migration is complete.
- Create a new hosted zone and DNS records in Amazon Route 53. Remove the Delegation Signer (DS) record from the parent zone in the current DNS service provider. Transfer domain registration to Amazon Route 53, where the DNSSEC will be automatically re-enabled. Update the NS records to use Route 53 name servers and monitor the traffic. Configure the TTL to 172800 seconds for the NS record once the migration is complete.
Question 8
A multinational organization plans to adopt a hybrid cloud infrastructure that requires a dedicated connection between its on-premises data center and virtual private cloud (VPC) in AWS. The connection must allow the cloud-based applications hosted in EC2 instances to fetch data from the organization’s on-premises file servers with a more consistent network experience than Internet-based connections.
Which of the following options should the Network team implement to satisfy this requirement?
- Set up a VPC Peering connection between the VPC and the on-premises data center.
- Set up an AWS Direct Connect connection between the VPC and the on-premises data center.
- Set up an Amazon Connect omnichannel connection between the VPC and the on-premises data center.
- Set up an AWS VPN CloudHub between the VPC and the on-premises data center.
Question 9
A company is launching a web application that will be hosted in an Amazon ECS cluster with an EC2 launch type. The Network Engineer configured the associated security group and network ACL of the instances to allow inbound traffic on ports 80 and 443. After the deployment, the QA team noticed that the application is unreachable over the public Internet.
What should the Engineer do to rectify this issue?
- Ensure that the security group has a rule that allows outbound traffic on port 80 and port 443.
- Verify that the network ACL has a rule that allows Inbound traffic on the ephemeral ports 1024 – 65535.
- Set the network mode to
bridgeto ensure that every task that is launched from the task definition gets its own elastic network interface (ENI) and a primary private IP address. - Ensure that the network ACL has a rule that allows Outbound traffic on the ephemeral ports 1024 – 65535.
Question 10
A Network Administrator is migrating an on-premises application to AWS Cloud to improve its scalability and availability. The application will be hosted in Amazon EC2 Instances that are deployed on a private subnet with an Application Load Balancer in front to distribute IPv4 traffic. The users of the application are internal employees only.
As part of its processing, the application will also pull massive amounts of data from an external API service over the Internet. The Administrator must allow the EC2 instances to fetch data from the Internet but prevent external hosts over the Internet from initiating a connection with the instances. When the application downloads data from the Internet, the connection must be highly available, and the bandwidth should scale up to 45 Gbps.
The solution must also support long-running queries and downloads initiated by the EC2 instances. Some requests may take a total of 10 minutes to complete.
What is the MOST suitable solution that the Administrator should implement?
- Launch a NAT Instance in a public subnet. Modify the route table to block any incoming traffic from the Internet. Configure TCP keepalive on the EC2 instances with a value of more than 600 seconds.
- Launch a NAT Gateway in a private subnet. Configure the route table to direct the outgoing Internet traffic from the private subnet to the NAT gateway. Enable TCP keepalive on the EC2 instances with a value of more than 600 seconds.
- Set up a Direct Connect Gateway with five 10 Gbps AWS Direct Connect connections. Associate Direct Connect Gateway to the Internet gateway of the VPC. Configure TCP keepalive on the EC2 instances with a value of less than 600 seconds.
- Launch a NAT Gateway in a public subnet. Update the route table to direct the outgoing Internet traffic from the private subnet to the NAT gateway. Enable TCP keepalive on the EC2 instances with a value of less than 600 seconds.
For more practice questions like these and to further prepare you for the actual AWS Certified Advanced Networking Specialty ANS-C01 exam, we recommend that you take our top-notch AWS Certified Advanced Networking Specialty Practice Exams, which have been regarded as the best in the market.
Also, check out our AWS Certified Advanced Networking Specialty ANS-C01 exam study guide here.