Microsoft Defender for Cloud Apps Cheat Sheet
- A Cloud Access Security Broker (CASB) solution that provides visibility, control, and threat protection for apps, users, and data across cloud environments.
- Helps organizations secure sanctioned and unsanctioned apps, enforce policies, and protect sensitive data in real time.
- Detects risky activities and anomalous behavior with advanced analytics and Microsoft threat intelligence.
- Supports regulatory compliance and governance by providing detailed audit logs, data classification, and automated controls.
Key Features
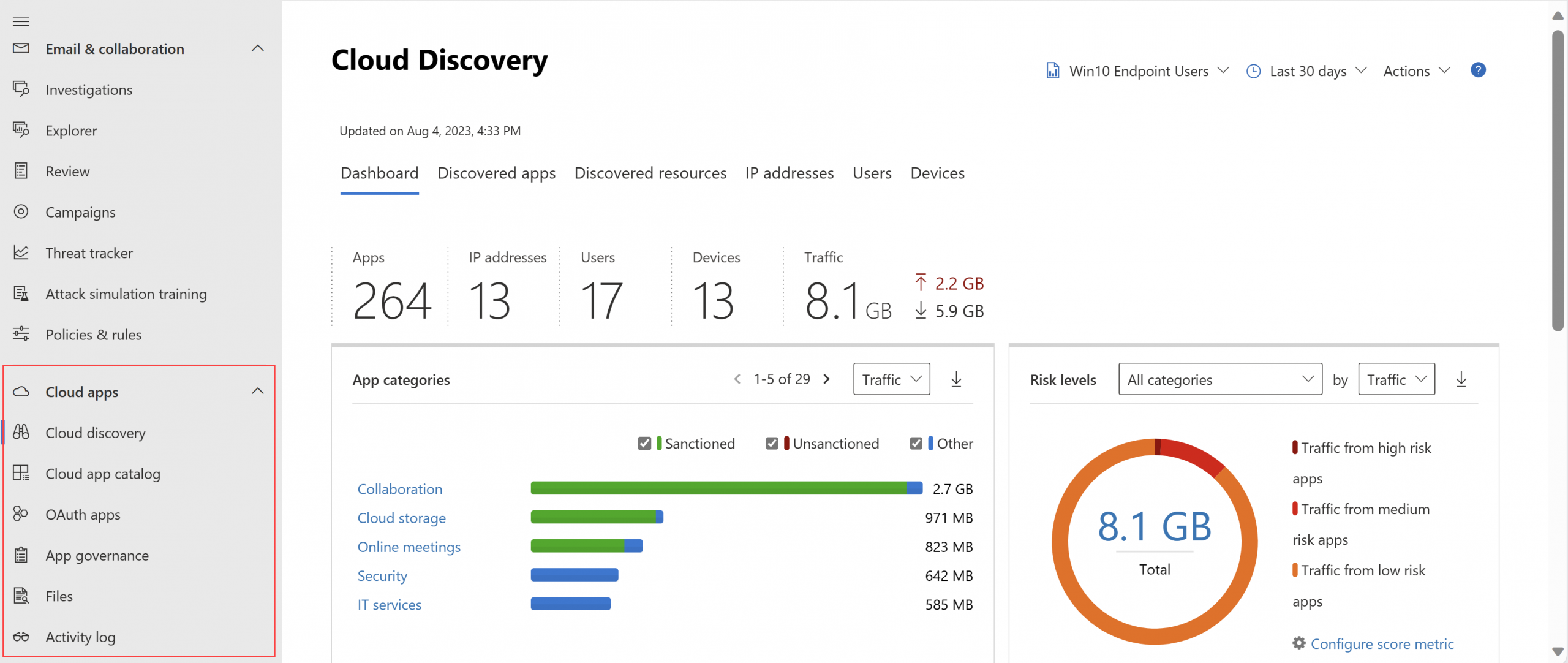
App Discovery / Shadow IT
- Uses traffic logs (firewall, proxy, Defender for Endpoint) to identify cloud apps used in the environment.
- Assigns risk scores based on 90+ indicators and enables assessment & prioritization.
SSPM (SaaS Security Posture Management)
- Provides misconfiguration recommendations per connected app using industry benchmarks.
- Integrates with Microsoft Secure Score to reflect cloud app posture.
Data Protection & DLP
- File policies: monitor, alert, or act on files (e.g. publicly shared, external sharing, sensitive label).
- Session policies: enforce controls in real time (e.g. block download, scan uploads/downloads, restrict copy/paste).
- Supports integration with Microsoft Purview Information Protection to apply sensitivity labels.
Threat and Anomaly Detection
- Detects unusual behavior (mass download, impossible travel, compromised accounts) via UEBA and machine learning.
- Integrates signals with Microsoft Defender XDR to correlate cross-vector incidents.
Conditional Access & Real-time Governance
- Works with Microsoft Entra ID to route cloud app traffic for controlling sessions (Conditional Access App Control).
- Governance actions: suspend a session, revoke token, quarantine files, block users, etc.
App Governance
- Monitors OAuth apps (permissions, unused permissions, overprivileged apps) and generates alerts.
- Provides app governance in Defender XDR for advanced insights.
Use Cases
- Discover and categorize shadow IT usage in your organization
- Enforce session-based controls on SaaS apps (e.g. stop download on unmanaged devices)
- Protect sensitive data stored or processed in cloud apps via DLP
- Detect compromised user accounts or insider threats
- Govern OAuth app permissions and reduce over-privileged apps
- Integrate alerts into SIEM / SOAR workflows (e.g. Microsoft Sentinel)
- Improve Secure Score by applying posture recommendations
Integrations with other Azure services
| Azure Service | Integration Capabilities |
| Microsoft Defender XDR (formerly Microsoft 365 Defender) | Correlate alerts from cloud apps with endpoints, identities, email, etc. |
| Microsoft Defender for Endpoint | Extend cloud discovery to managed devices |
| Microsoft Entra ID | Conditional Access App Control routing, identity-based policy enforcement |
| Microsoft Purview | Use sensitivity labels in file policies and coordinate classification & DLP |
| Microsoft Sentinel | Stream alerts, incidents, and logs to unified security operations workflows |
| Microsoft Defender Portal | Manage Defender for Cloud Apps together with other Defender services in this console. |
Important terminologies
- App Connector: API integration enabling activity, file, and governance visibility
- Cloud Discovery: The process of analyzing traffic or logs to find which cloud apps are used
- Shadow IT: Discovery of unmanaged or unsanctioned cloud apps using traffic logs from firewalls and proxies.
- Policy Template / Policy: Prebuilt detection or control patterns (activity, session, file, OAuth)
- Session Policy: Real-time enforcement applied during a session (upload scan, block download, restrict clipboard)
- File Policy: For static data (files) in apps; defines conditions (sharing, sensitivity) and actions (alert, quarantine)
- App Governance: Monitoring and controlling OAuth app permissions, usage, and anomalies
- Session controls: Real-time restrictions applied to user sessions, such as blocking downloads or monitoring uploads.
How to access
- Prerequisites
- You should have the appropriate license (Microsoft 365 E5).
- You must have the right permissions in Microsoft Entra ID (e.g., Global Administrator, Security Administrator) or Microsoft 365.
- Deployment steps
- Sign in to the Microsoft Defender portal.
- In the navigation pane, select Cloud Apps.
- You can configure app connectors, policies, and Cloud Discovery settings from there.
Microsoft Defender for Cloud Apps Cheat Sheet References:
https://learn.microsoft.com/en-us/defender-cloud-apps/what-is-defender-for-cloud-apps
https://learn.microsoft.com/en-us/defender-cloud-apps/get-started
https://learn.microsoft.com/en-us/defender-cloud-apps/microsoft-365-security-center-defender-cloud-apps
https://learn.microsoft.com/en-us/defender-cloud-apps/cas-compliance-trust