Last updated on December 26, 2025
Amazon Cognito Cheat Sheet
- A user management and authentication service that can be integrated into your web or mobile applications. Amazon Cognito enables authentication through external identity providers and provides temporary AWS credentials to access your app’s backend resources or any service behind Amazon API Gateway.
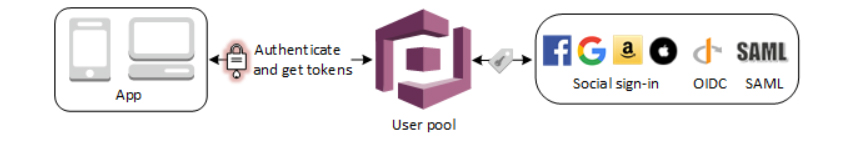
- It supports SAML, OpenID Connect (OIDC), and social identity providers (Facebook, Twitter, Amazon, Google, Apple, Microsoft, LinkedIn), as well as your own identity provider.
- All Cognito ID tokens are represented as JSON Web Tokens (JWT).
Features
-
AWS PrivateLink Support: Supports PrivateLink for user pools and identity pools, allowing API requests through VPC endpoints.
-
Passkeys and One-Time Passwords: Users can now sign in with passkeys and one-time passwords.
-
Managed Login Enhancements: Add terms & conditions and privacy policy links, apply AWS WAF web ACLs, and control reauthentication with the prompt parameter.
-
Identity Pool Enhancements:
-
Improved IAM role trust policies scoped for OIDC federation.
-
Includes example applications to demonstrate functionality.
-
-
Refresh Token Rotation & M2M Improvements:
-
Rotate and invalidate refresh tokens in refresh-token requests.
-
Pass client metadata in machine-to-machine (M2M) requests via pre token generation Lambda triggers.
-
-
Resource Binding & Token Customization:
-
Access tokens now support RFC 8707 resource binding for audience verification.
-
Pre token generation Lambda triggers can modify claims, scopes, and include complex objects for user and machine identities.
-
-
Lambda Integration Updates: Supports Node.js 22.x for custom email/SMS triggers; triggers available for Pre Sign-up, Post Confirmation, Pre Authentication, and user migration flows.
-
Regional Expansions: Cognito now available in Mexico (Central), Thailand, Malaysia, Canada West (Calgary), Hong Kong, Spain, Hyderabad, Melbourne, Zurich, UAE.
-
Advanced Security Updates: New guidance for securing user pool secrets, adaptive authentication enhancements, threat protection for custom authentication flows, password reuse prevention, user activity log export, and MFA logic diagrams.
How It Works
User Pools
-
-
User pools are user directories that provide sign-up and sign-in options for your app users.
-
Users can sign in to your web or mobile app through Amazon Cognito, or federate through a third-party identity provider (IdP).
-
You can use the aliasing feature to enable your users to sign up or sign in with an email address and a password or a phone number and a password.
-
User pools are each created in one AWS Region, and they store the user profile data only in that region. You can also send user data to a different AWS Region.
-
Tokens provided through user pools:
-
Access tokens contain scopes and groups and are used to grant access to authorized resources. Access tokens can be configured to expire in as little as five minutes or as long as 24 hours.
-
Refresh tokens contain the information necessary to obtain a new ID or access token. Refresh tokens can be configured to expire in as little as one hour or as long as ten years.
-
-
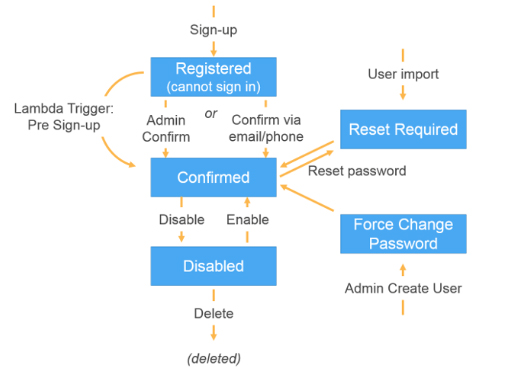
Manage Users: After you create a user pool, you can create, confirm, and manage users accounts. Amazon Cognito User Pools groups lets you manage your users and their access to resources by mapping IAM roles to groups.
-
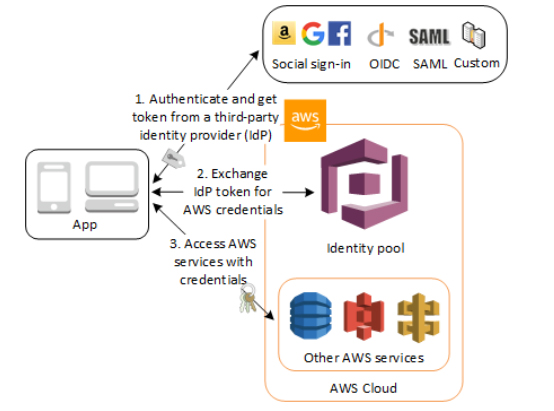
Identity Pools
-
-
Use this feature if you want to federate users to your AWS services.
-
Identity pools enable you to grant your users temporary AWS credentials to access AWS services, such as Amazon S3 and DynamoDB.
-
Supports:
-
Amazon Cognito user pools
-
Social sign-in with Facebook, Google, and Login with Amazon
-
OpenID Connect (OIDC) providers
-
SAML identity providers
-
Developer authenticated identities
-
Unauthenticated identities (guest users).
-
-
To save user profile information, your identity pool needs to be integrated with a user pool.
-
The permissions for each authenticated and non-authenticated user are controlled through IAM roles that you create.
-
Once you have an OpenID Connect token, you can then trade this for temporary AWS credentials via the
AssumeRoleWithWebIdentityAPI call in AWS Security Token Service (STS).
-
Common Use Cases
-
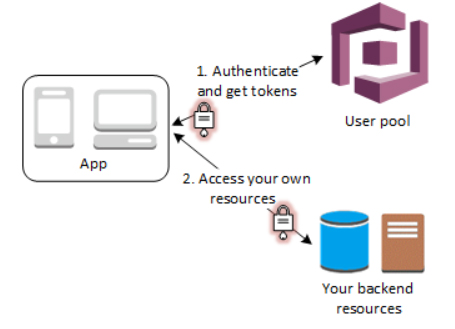
- Enable your users to authenticate with a user pool.
-
- After a successful user pool sign-in, your web or mobile app will receive user pool tokens from Amazon Cognito. You can use those tokens to control access to your server-side resources.
-
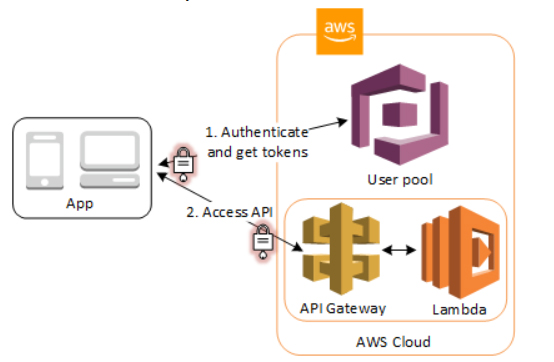
- Access resources with API Gateway and Lambda with a User Pool. API Gateway validates the tokens from a successful user pool authentication, and uses them to grant your users access to resources including Lambda functions, or your own API.
- Access resources with API Gateway and Lambda with a User Pool. API Gateway validates the tokens from a successful user pool authentication, and uses them to grant your users access to resources including Lambda functions, or your own API.
-
- After a successful user pool authentication, your app will receive user pool tokens from Amazon Cognito. You can exchange them for temporary access to other AWS services with an identity pool.
- After a successful user pool authentication, your app will receive user pool tokens from Amazon Cognito. You can exchange them for temporary access to other AWS services with an identity pool.
-
- Enable your users access to AWS services through an identity pool. In exchange, the identity pool grants temporary AWS credentials that you can use to access other AWS services.
- Enable your users access to AWS services through an identity pool. In exchange, the identity pool grants temporary AWS credentials that you can use to access other AWS services.
-
- Grant your users access to AWS AppSync resources with tokens from a successful Amazon Cognito authentication (from a user pool or an identity pool).
- Amazon Cognito is also commonly used together with AWS Amplify, a framework for developing web and mobile applications with AWS services.
- Application Authentication (User Pools)
-
Scenario: Your mobile or web app needs a secure sign-up and sign-in directory.
-
Flow: Users sign in via Cognito User Pools (or social providers). Upon success, the app receives standard JWTs (ID, Access, and Refresh tokens). You can use these tokens to control access to your application’s pages or components.
- Serverless API Authorization
-
Scenario: You are protecting a serverless API built with API Gateway and Lambda.
-
Flow: Configure a Cognito Authorizer on API Gateway. It automatically validates the User Pool tokens attached to incoming API requests before allowing them to trigger your Lambda functions.
-
- Direct AWS Resource Access (Identity Pools)
-
Scenario: Your mobile app needs to upload files directly to S3 or read from DynamoDB without passing through a backend server.
-
Flow: The app authenticates with a User Pool, then swaps the JWT for temporary AWS credentials (Access Key/Secret Key) via an Identity Pool. These credentials allow the app to talk directly to AWS services.
- User Data Synchronization (AWS AppSync)
-
Scenario: You need to sync user profile data, game state, or settings across multiple devices (e.g., phone and tablet) in real-time.
-
Flow: Use User Pool tokens to authenticate with AWS AppSync. AppSync uses GraphQL to securely synchronize data across devices, supporting both online and offline modes.
-
Legacy: Amazon Cognito Sync
-
Status: Deprecated.
-
Function: Previously used to sync user data (preferences, game state) across devices.
-
Recommendation: AWS now advises using AWS AppSync for syncing user data across devices. Cognito Sync is maintained for existing apps but should not be used for new workloads.
- Advanced Security Features
-
-
Threat Protection (Advanced Security): Available in the Cognito Plus tier.
-
-
Adaptive Authentication: Detects unusual sign-in activity (new location, device, etc.). It assigns a risk score and can automatically block the request or require MFA.
-
Compromised Credentials Detection: Checks if a username/password pair has been compromised in known data breaches elsewhere on the internet and prompts a password change.
-
-
MFA: Users can verify their identities using SMS, email, or Time-based One-time Password (TOTP) generators.
-
- Integration with AWS Lambda
- You can trigger Lambda functions during user pool operations (e.g., Pre Sign-up, Post Confirmation, Pre Authentication).
- Synchronous Invocation: Amazon Cognito invokes these functions synchronously. The function must respond within 5 seconds; otherwise, the call is retried (up to 3 times) before timing out.
- Migration: You can use a Lambda trigger to migrate users from an existing directory into a User Pool seamlessly as they sign in
Amazon Cognito Pricing
-
MAU Billing:
-
Lite + Essentials: First 10,000 MAUs free.
-
Plus Tier: Charged from the first user (no free tier).
-
-
Machine-to-Machine (M2M): Charged per token request.
-
MFA: Standard AWS SNS (SMS) and SES (Email) charges apply for verification messages.
Note: If you are studying for the AWS Certified Security Specialty exam, we highly recommend that you take our AWS Certified Security – Specialty Practice Exams and read our Security Specialty exam study guide.
Validate Your Knowledge
Question 1
A Software Engineer has developed a web application to monitor the pending/processed orders on the corporate sales server. The application needs to be accessed by Delivery, Finance, and Admin teams. The Security Administrator decided to integrate Amazon Cognito to the application to provide user sign-in functionality for the members of each team. The Delivery team should be able to update entries on the application while the Finance team only needs read permissions to verify the flow of orders.
Which of the following options will help the Administrator grant distinct permissions for each team member?
- Amazon Cognito User Pool Groups
- Amazon Cognito Identity Pool
- Amazon Cognito Sync
- Amazon Cognito Federated Identities
For more AWS practice exam questions with detailed explanations, visit the Tutorials Dojo Portal:
Amazon Cognito Cheat Sheet Resources:
https://aws.amazon.com/cognito/
https://aws.amazon.com/cognito/faqs/
https://docs.aws.amazon.com/cognito/latest/developerguide/what-is-amazon-cognito.html
Overview of Amazon Cognito User Pools and Federated Identities