Last updated on December 26, 2025
Amazon Inspector Cheat Sheet
-
Amazon Inspector is an automated vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure.
-
Legacy Note: This service replaces “Amazon Inspector Classic.” Inspector Classic required manual scheduling and custom agents; the new Inspector is continuous, automated, and integrated with AWS Organizations.
-
-
Key Capabilities
-
- Continuous Scanning: Automatically detects and scans new resources; rescans whenever changes occur (new software, new CVEs, infrastructure changes).
- Multi-Resource Coverage: Scans Amazon EC2, Amazon ECR container images, AWS Lambda functions, and Developer Code (CI/CD pipelines).
- Centralized Management: Integrated with AWS Organizations, allowing delegated administrators to manage findings across all accounts.
- Scan Mode: Inspector automatically chooses agent-based (SSM) or agentless scanning for EC2 instances.
Features
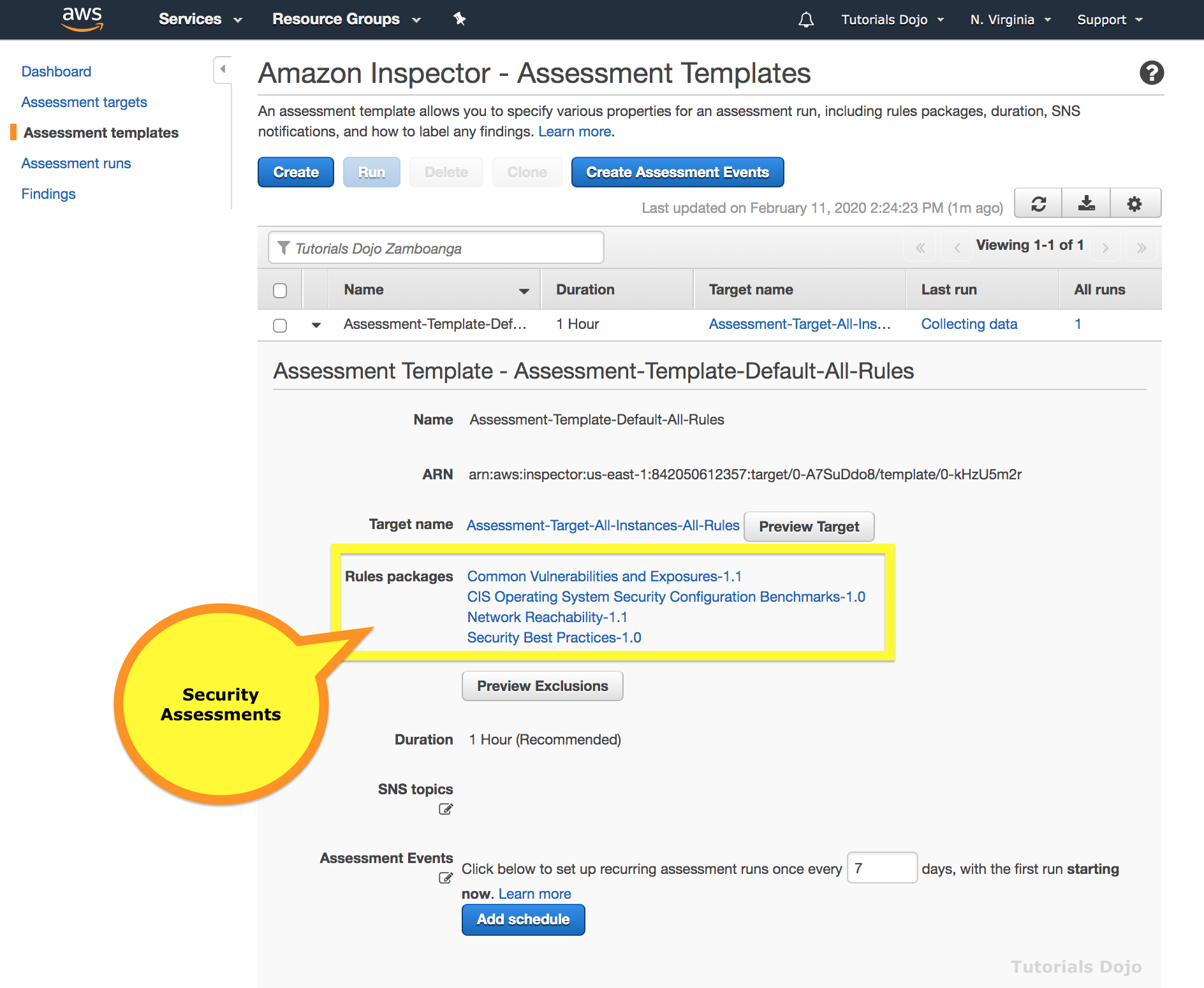
- Inspector provides an engine that analyzes system and resource configuration and monitors activity to determine what an assessment target looks like, how it behaves, and its dependent components. The combination of this telemetry provides a complete picture of the assessment target and its potential security or compliance issues.
- Inspector incorporates a built-in library of rules and reports. These include checks against best practices, common compliance standards and vulnerabilities.
- Automate security vulnerability assessments throughout your development and deployment pipeline or against static production systems.
- Inspector is an API-driven service that uses an optional agent, making it easy to deploy, manage, and automate.
- SBOM Generator: Generates Software Bill of Materials, tracks license info, scans Dockerfiles/images for misconfigurations, and exports SBOMs.
- SSM Plugin CVE Suppression: Suppresses false positives for CVEs (e.g., CVE-2025-61729, CVE-2025-58188).
- AWS Organizations Policies: Centralized enablement, governance, and delegation for multiple accounts.
- Resource Support Updates:
- EC2: Fedora 42, Ubuntu 25.04; MacOS supported; removed Oracle Linux 7, SLES 15.5, Fedora 39.
- ECR: Alpine 3.22, Fedora 42, Ubuntu 25.04; removed Alpine 3.17.
- Lambda: Node.js 202.x, Python 3.13, AL2 runtime.
- BusyBox: Supported for scanning.
- First-party & third-party code scanning: Includes dependencies and IaC.
- Container Image Usage: Tracks actively used images and last-used timestamps.
- Agentless EC2 Scanning: Scans instances without SSM agents via EBS snapshot analysis.
- CIS Benchmark Assessments: Runs on-demand or scheduled compliance checks.
- CI/CD Integrations: GitHub Actions, CodePipeline, CodeCatalyst.
- Lambda Code Scanning: Encrypts findings, provides remediation suggestions.
- ECR Re-scan Refresh: Updates scan duration on push/pull events.
- Findings Retention Update: Closed findings for deleted or terminated resources removed after 3 days.
Concepts
- Findings: Potential security issues detected during scans (exploitable vulnerabilities, network exposure, package risks, code issues).
- Severity Levels:
-
Critical / High / Medium / Low — indicate risk impact on confidentiality, integrity, or availability.
-
Informational — highlights non-critical configuration details.
-
- Network Exposure Analysis: Inspector determines whether EC2 instance ports are reachable from external sources (e.g., internet gateway, VPC peering, VPN). It highlights overly permissive security groups, ACLs, and other misconfigurations.
- Resource Inventory: Inspector collects metadata such as installed packages, versions, Lambda layers, container base images, and software dependencies.
Scanning Engines
-
EC2 Scanning:
-
Agent-Based (SSM): Uses the AWS Systems Manager (SSM) Agent to inspect the software inventory of instances. No separate “Inspector Agent” is required.
-
Agentless (Hybrid): Scans EC2 instances without an agent by taking a snapshot of the EBS volume and analyzing it. Useful for unmanaged or “hardened” instances where agents cannot be installed.
-
-
ECR Scanning:
-
On-Push: Scans container images automatically when they are pushed to the registry.
-
Continuous: Continuously re-scans images when new vulnerabilities (CVEs) are added to the database.
-
-
Lambda Scanning:
-
Standard Scanning: Scans application dependencies (e.g., Python
pippackages, Node.jsnpmmodules) within the Lambda function and layers. -
Code Scanning: Scans your custom application code for security vulnerabilities (e.g., injection flaws, data leaks, hardcoded secrets).
-
-
CIS Benchmarks:
-
Runs on-demand or scheduled assessments against Center for Internet Security (CIS) configuration benchmarks for operating systems (e.g., “CIS Amazon Linux 2 Benchmark Level 1”).
-
Assessment Reports
- Inspector findings can be exported or viewed in the AWS Console or Security Hub.
- Findings report includes:
-
Executive summary
-
Affected resources (EC2, Lambda, ECR, etc.)
-
Vulnerability details and CVE references
-
Recommended remediation steps
-
Package or code component involved
-
- You can generate detailed exportable reports for audits or compliance reviews.
Amazon Inspector Pricing
- Pricing depends on the resource type scanned.
| Resource Type | Feature | Estimated Cost (US East 1) |
|---|---|---|
| EC2 Instances | Agent-Based (SSM) | ~$1.25 per instance/month |
| Agentless | ~$1.75 per instance/month | |
| ECR Containers | Initial Image Scan | $0.09 per image pushed |
| Continuous Rescan | $0.01 per rescan | |
| AWS Lambda | Standard Scanning | $0.30 per function/month |
| Code Scanning | +$0.60 per function/month (Total: $0.90) | |
| Code Security | CI/CD / Repository | $0.15 per scan |
Note: If you are studying for the AWS Certified Security Specialty exam, we highly recommend that you take our AWS Certified Security – Specialty Practice Exams and read our Security Specialty exam study guide.
Amazon Inspector Cheat Sheet References:
https://docs.aws.amazon.com/inspector/latest/userguide
https://aws.amazon.com/inspector/pricing/
https://aws.amazon.com/inspector/faqs/