Last updated on July 11, 2024
Even before the Internet, the security, privacy, and integrity of information have always been the top concern of institutions like banks, hospitals, and universities. Nobody wants their personal information (name, address, credit card number, etc.) to be exposed in public for anyone to use. Imagine signing up on your favorite social media website, and after a few days, somewhere on the globe has been using your profile and pretending to be you without you knowing! Or maybe you’ve been using your credit card for shopping online and suddenly, your bank is sending you email reports for fraudulent activities on your account. That would be a creepy and scary world to live in.
The unfortunate truth is that no matter how secure you might think your system is, it will never be one hundred percent secure. There will always be loopholes, and as computers get even more powerful, common attacks like brute force will still be a valid threat. For this reason, tremendous efforts have been made to improve and mitigate scenarios where sensitive data are compromised. Encryption proves to be the most effective solution in battling data breaches.
What is Encryption?
Encryption is the process of converting the information (plaintext) into secret code (ciphertext) to hide its original meaning. It is used to protect the data so that only authorized users can read it.
It uses the concept of “keys” which are used to encrypt and decrypt the sensitive information from one end to another. The idea is, without these keys, one cannot simply decrypt and read the hidden information.
There are two types of encryption:
Symmetric encryption – uses a single key for both encryption and decryption. The shared key must be sent together with the encrypted data in order for other parties to read it.
Because of the simplicity of the process, it is usually faster than asymmetric encryption and is efficient in encrypting large amounts of data.
Symmetric Encryption Disadvantage:
The main disadvantage of using a symmetric key is the difficulty of transporting the shared key. It is difficult in the sense that attacks, like man-in-the-middle attack, could easily obtain both the key and the encrypted data. Since a single key is used for both encryption and decryption, the man behind the attack would be able to decrypt the information sent over the network.
Asymmetric encryption – it uses a mathematically related public and private key for encryption and decryption. The public key is used for encrypting data and can never be used for decryption. The private key is only used for decrypting data. The private key stays on the user while both the public key and the encrypted data is sent to other parties. This kind of method makes the sharing of public keys a lot easier because even if someone has managed to steal the data with the public key, he won’t be able to decrypt the information.
Since this type of encryption uses a more complex algorithm than symmetric encryption, asymmetric is used for systems that use small data. It is usually used for establishing secure connections like TLS and SSH. It is also slower than symmetric encryption and is inefficient for encrypting large data.
Symmetric and Asymmetric Keys In AWS Key Management System:
AWS KMS keys
AWS KMS keys are the main resource in AWS KMS. They can be used to encrypt, decrypt, and re-encrypt data, as well as generate data keys for use outside of AWS KMS.
Three types of AWS KMS Keys:
- Customer Managed keys
- You can view the KMS key’s metadata
- You can manage the KMS keys
- It is used only for your account
- Automatic rotation is optional
- AWS managed keys
- You can view the KMS key’s metadata but you cannot manage it.
- It is used only for your account
- Automatic rotation is required
- AWS owned keys
- These are KMS keys that an AWS Service owns and manages for use in multiple AWS accounts.
- You do not need to create or manage the AWS owned keys.
- The key rotation strategy for an AWS owned keys is determined by the AWS service that creates and manages the KMS keys.
AWS KMS key supports both symmetric and asymmetric encryption. Although integrated in AWS Cloud, the concepts behind the encryption are still the same as the one explained above.
Symmetric encryption KMS keys
- Represents a 256-bit encryption key that never leaves AWS KMS unencrypted.
- A Symmetric encryption KMS key type is created by default when you call the create-key API without specifying a value for the –key-spec parameter. The –key-spec parameter allows you to define the KMS key specification, where you can choose between symmetric and asymmetric key types.
- AWS services that are integrated with AWS KMS (Amazon DynamoDB, Amazon S3, Amazon Relational Database Service, etc.) use symmetric encryption KMS key to encrypt and decrypt data and do not support Asymmetric KMS keys.
- You can import your own key material into a symmetric encryption KMS keys and create symmetric KMS keys in custom key stores.
- Note that imported key material is supported only for symmetric encryption KMS keys.
Asymmetric KMS keys
- Private Key
- The private key is created in AWS KMS and never leaves AWS KMS unencrypted.
- The private can only be used by calling AWS KMS.
- Public Key
- The public key can be used within or outside of AWS KMS.
Three types of asymmetric KMS keys
- RSA KMS keys
- Can be used for encryption and decryption or signing and verification. You can never use RSA KMS keys for both purposes at the same time.
- Elliptic Curve (ECC) KMS keys
- Elliptic curve key pair used for signing and verification or serving shared secrets. You can never use Elliptic Curve (ECC) KMS keys for both purposes at the same time.
- SM2 KMS keys
- Applicable only in China regions.
- Can be used for encryption and decryption, signing and verification, or deriving shared secrets. You only need to choose one key usage type.
Use Case
- Symmetric
- Use symmetric if you are encrypting data within the AWS service. Since AWS services integrated with AWS KMS only support symmetric encryption KMS keys, there is no sense to use asymmetric KMS keys.
- Symmetric encryption is commonly used when encrypting data at rest. AWS uses symmetric encryption when you’re encrypting objects stored in an S3 bucket or enabling encryption for your EBS volumes.
- Asymmetric
- Since you can use the public key outside of AWS KMS in asymmetric, it is a good choice if you are building applications for users who cannot call AWS KMS. The easy process of creating key pairs is one of the main benefits of it.
- Applicable for data signing and verification. You can use asymmetric KMS keys to authenticate documents by using a digital signature. Digital signing is used to ensure the integrity of data that passes between networks. Suppose that a contract form is sent to you from your client. And you must ensure that the information within the contract is all true and has not been altered by third-parties. If you have the right key, you can cryptographically verify that the contract is indeed sent from your client.
Encryption and Decryption with AWS KMS API Demo
Requirements for this demo:
- Make sure that you have programmatic access to call AWS KMS API.
- We will be using Windows 10, so you need to download, install, and configure the latest version of AWS CLI for windows.
- We will also need to use a package called certutil to decode base64 encoded data. You can easily download it from google. Just search for certutil.
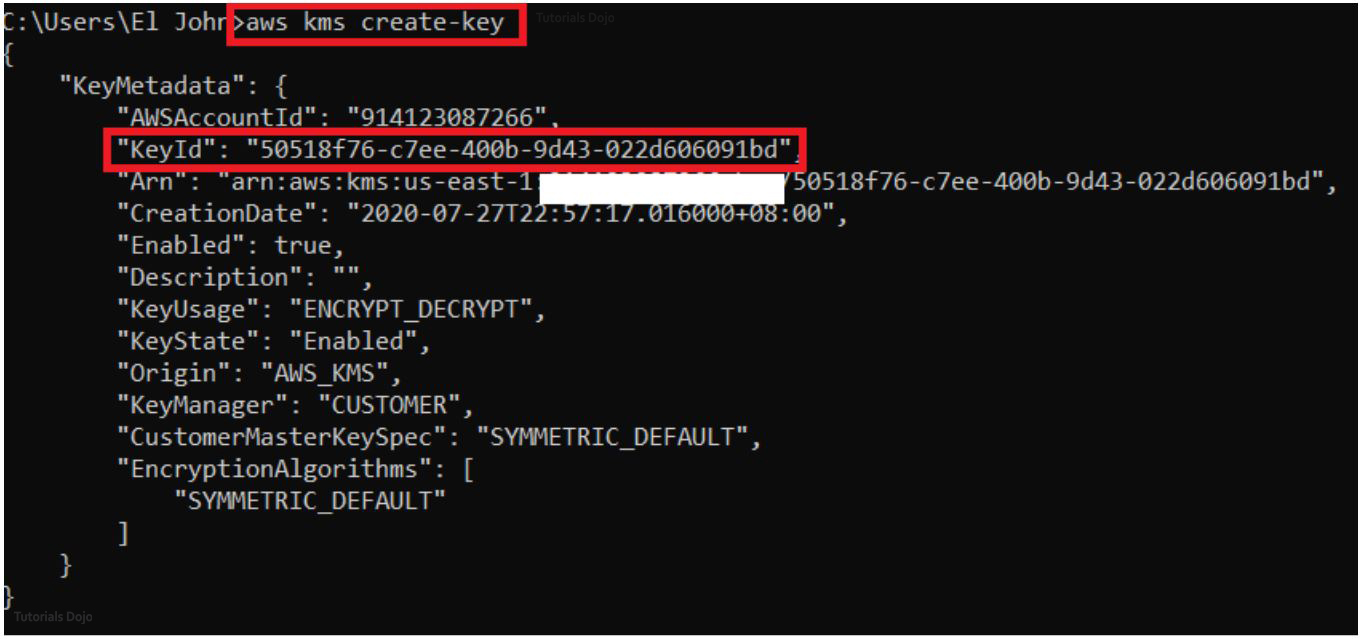
STEP 1. Create a symmetric key. For simplicity, let’s leave everything to default.
Type “aws kms create-key” on the command prompt. Store the key Id somewhere. We will use this to create an alias. An Alias is just a nickname to reference the key Id so that we won’t have to memorize it or type this long string everytime we need it.
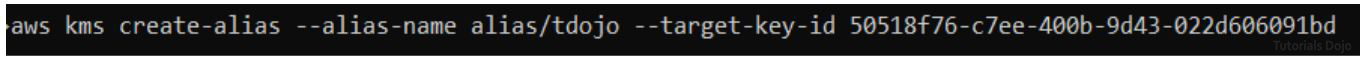
STEP 2. Create an alias. After the “–alias-name” parameter, type your preferred alias. Note that the custom name should be after the word “alias/” for it to work. Paste the key id after the “–target-key-id” parameter.
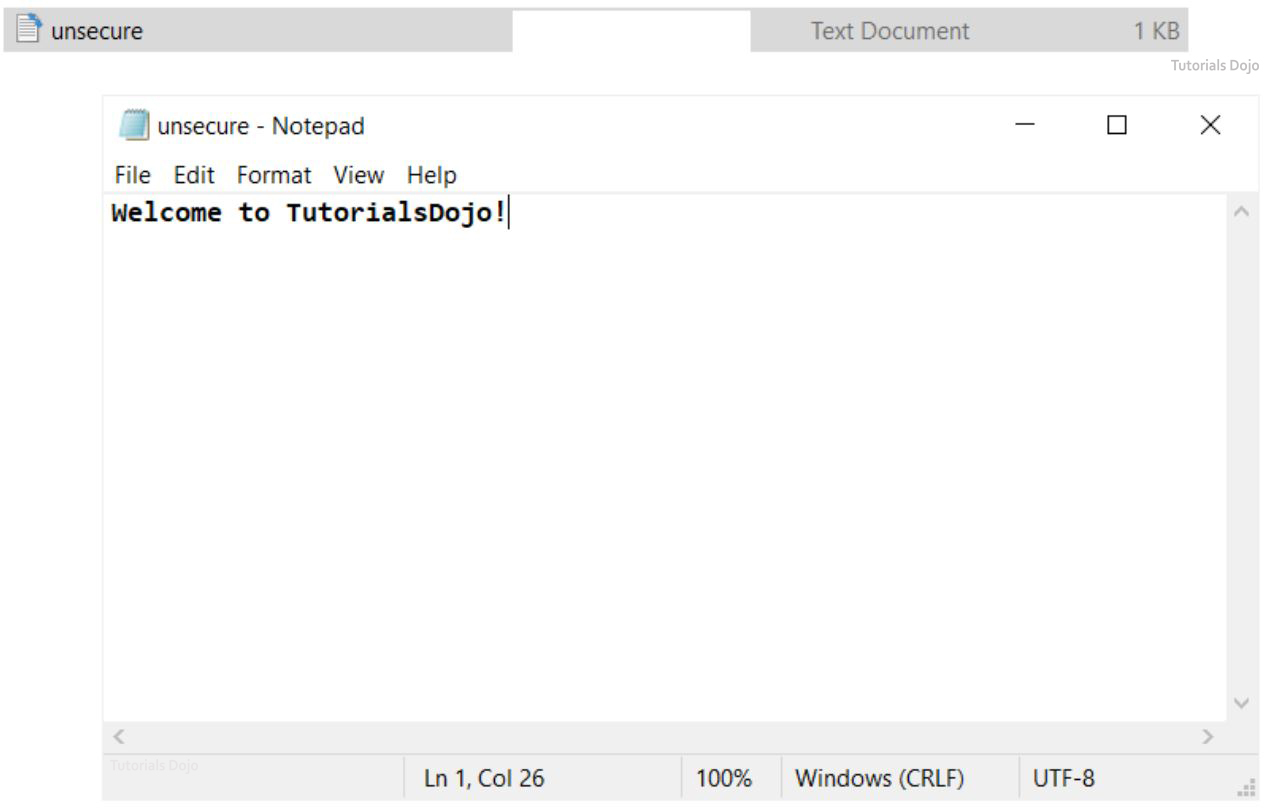
STEP 3. Let’s create a file that we will be encrypting and decrypting. To make it simple, let us create a txt file named “unsecure” and insert some text on it.
STEP 4. Encrypt the “unsecure.txt” file. The value for the “–plaintext” parameter should follow this format “fileb://<path-to-your-file>”. The output of this API call is base64 encoded. We will use the “–query” parameter to pipe the output into a file called “encrypted.base64”. You are free to name the file whatever you want. The output parameter ensures that the text generated will not be enclosed within quotes ( “” ).
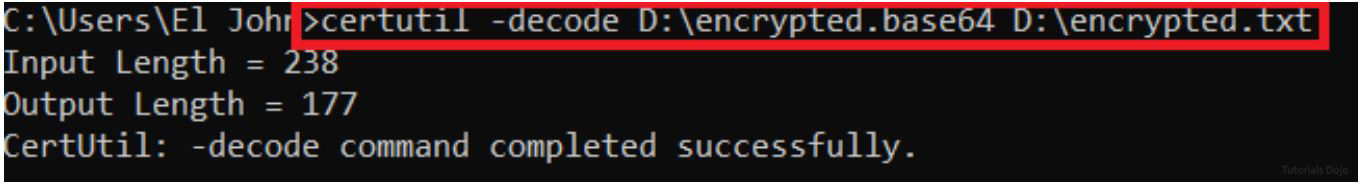
STEP 5. Let us convert the base64 encoded file to txt file using certutil.
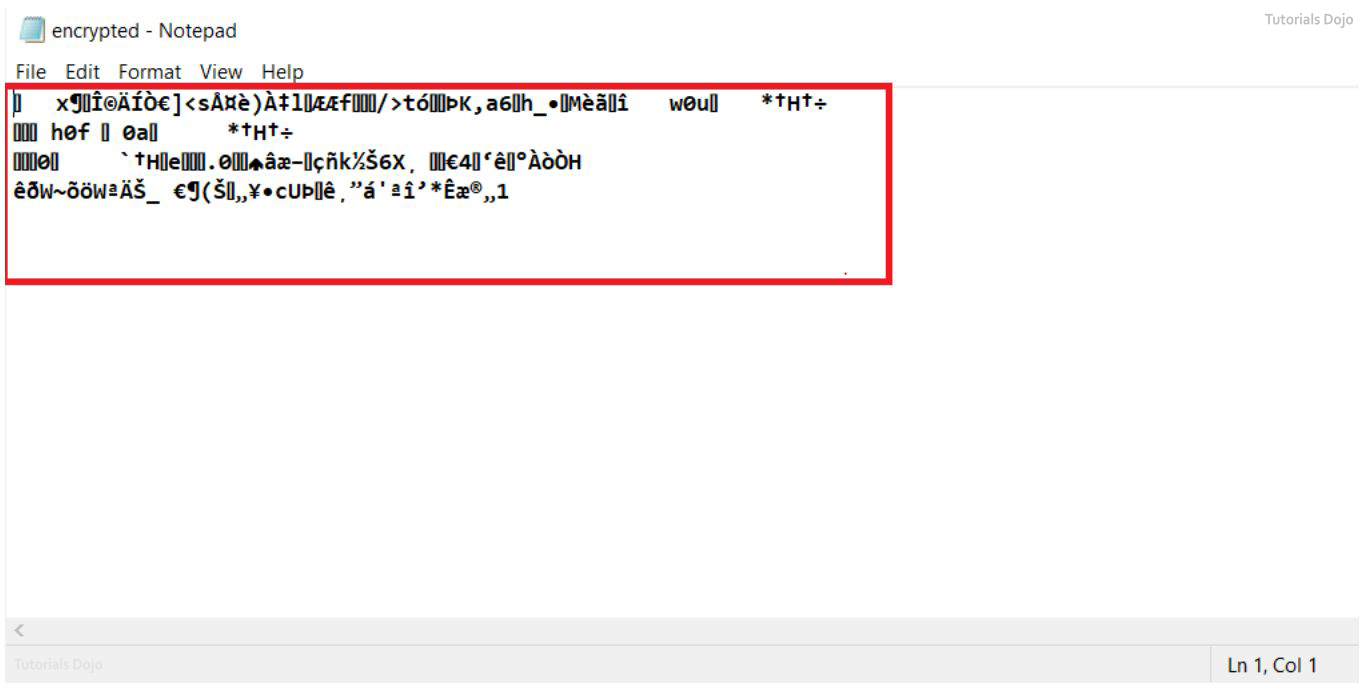
Open the text file. The “Welcome to TutorialsDojo” text that we created earlier has now turned into an unrecognizable text. This implies that we have successfully encrypted the file.
STEP 6. Now that we have successfully encrypted the data. Let us turn it back and decrypt the message. Call the decrypt API on the command prompt. Note that instead of the “–plaintext” parameter, we are using the –ciphertext-blob parameter.
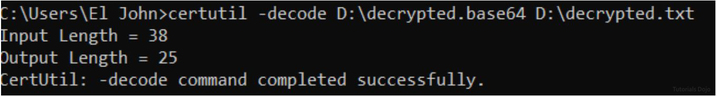
STEP 7. Again, let us convert the base64 file to a text file using the “certutil decode” command.
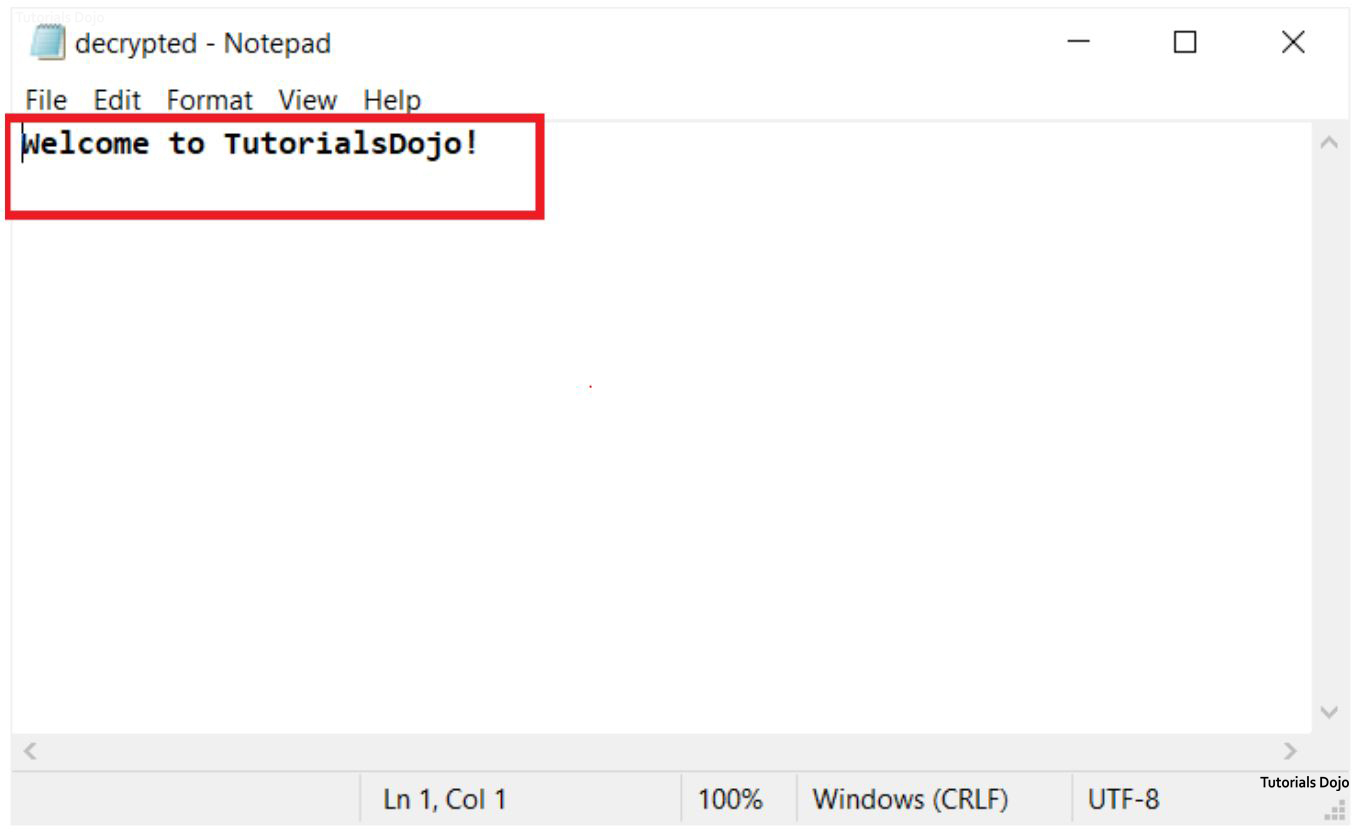
STEP 8. Open the “decrypted.txt” file. We have successfully decrypted the message using a single key. You can now see the message that we have written earlier. Good job following along!
In this tutorial, we have learned how to perform encryption and decryption by calling the AWS KMS API using the Amazon CLI on a command prompt. What we have done is a simple operation using one symmetrical encryption KMS key. You can play around the different parameters for your use case.
This article was taken from our AWS Certified Security Specialty study guide eBook:
If you are preparing for the AWS Security Specialty exam, we highly recommend that you grab a copy of our eBook and also simulate the exam with our AWS Certified Security Specialty Practice Exams.
References:
https://docs.aws.amazon.com/kms/latest/developerguide/symmetric-asymmetric.html
https://docs.aws.amazon.com/kms/latest/developerguide/symm-asymm-compare.html