The cybersecurity landscape is evolving rapidly because AI-powered cyberattacks are becoming more advanced. In particular, attackers leverage artificial intelligence (AI) to automate phishing, bypass traditional defenses, and target machine learning models. Consequently, these AI-powered cyberattacks are faster, more sophisticated, and harder to detect than ever before.
Fortunately, AWS provides a suite of AI-driven security services. Moreover, these services enable organizations to detect, prevent, and respond to modern threats, thereby keeping applications, data, and workloads safe in the cloud.
Understanding AI-Powered Cyberattacks
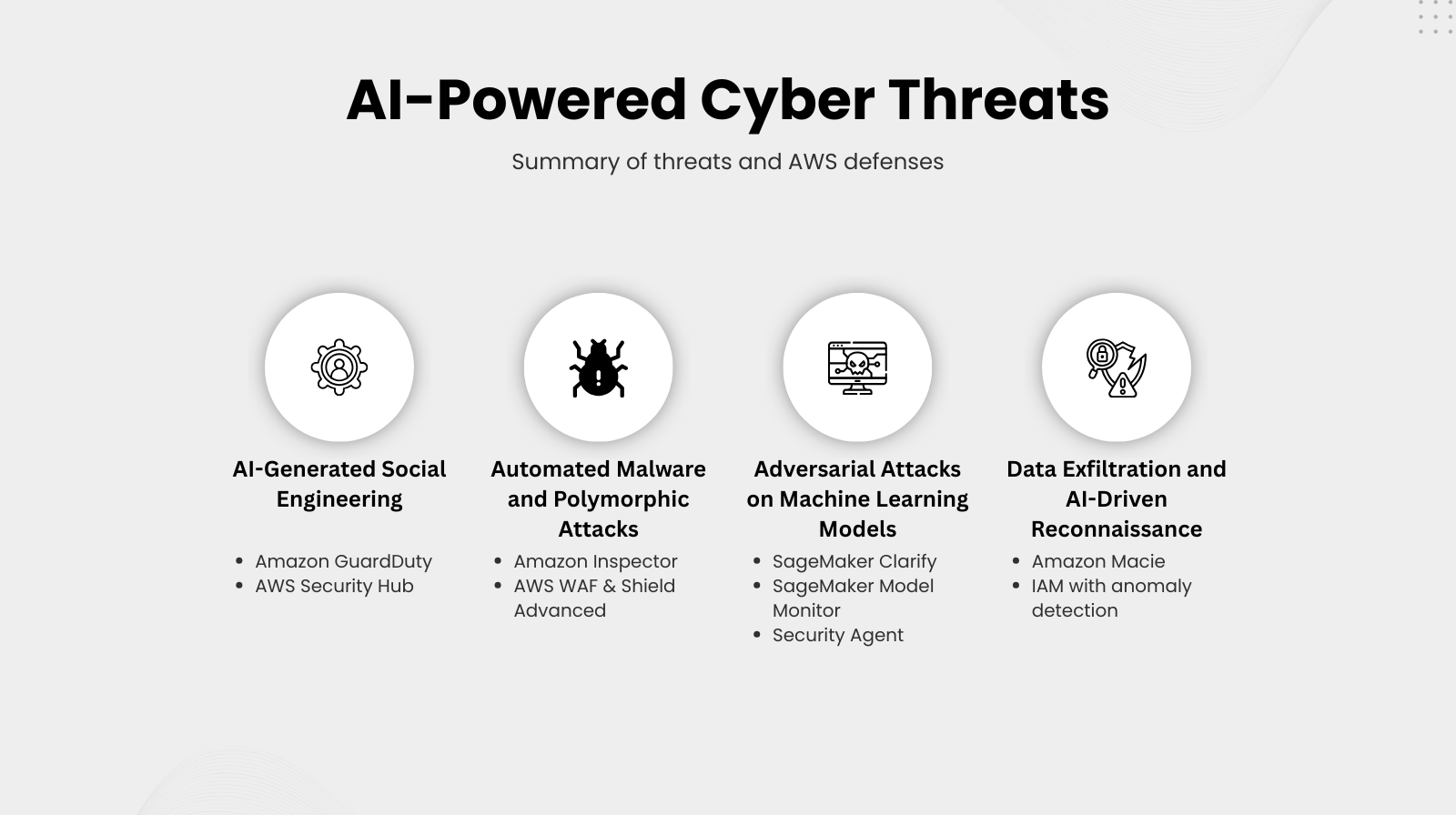
AI-Generated Social Engineering
- Attackers use AI to craft emails, SMS messages, or voice/video deepfakes that are indistinguishable from human-generated content. As a result, employees or customers are tricked into sharing credentials, clicking malicious links, or transferring funds. To counter this, Amazon GuardDuty detects suspicious logins or unauthorized access triggered by compromised credentials, while AWS Security Hub correlates alerts across multiple accounts to detect patterns of anomalous behavior. In practice, implementing AI-driven email filtering and anomaly detection can flag potential AI-generated messages before harm occurs.
Automated Malware and Polymorphic Attacks
- Malware mutates with every execution, evading signature-based antivirus solutions and endpoint protections. Therefore, traditional defenses fail, allowing malware to persist undetected. To mitigate this risk, Amazon Inspector continuously scans EC2 instances and container images for vulnerabilities. In addition, AWS WAF & Shield Advanced uses machine learning to detect anomalous traffic patterns and automatically block suspicious requests. For instance, AI-generated ransomware that changes payload signatures every few minutes can be detected at the network layer with Shield Advanced and at the host layer with Inspector.
Adversarial Attacks on Machine Learning Models
- Attackers craft inputs that manipulate ML models into producing incorrect predictions, such as bypassing fraud detection. Consequently, organizations may experience financial loss, degraded ML performance, or operational disruptions. To address this, SageMaker Clarify detects data drift and model bias, while SageMaker Model Monitor alerts when inputs are unusual or maliciously crafted. Furthermore, integrating security agents in CI/CD pipelines helps validate ML inputs and prevents deployment of compromised models. As a best practice, adversarial testing should be deployed before production deployment.
Data Exfiltration and AI-Driven Reconnaissance
- AI bots scan cloud environments to identify sensitive data, misconfigurations, and vulnerabilities. As a result, organizations are at risk of intellectual property theft, privacy violations, and compliance issues. Accordingly, Amazon Macie uses machine learning to detect unusual access patterns or potential data leaks in S3 buckets, and IAM with anomaly detection identifies abnormal access or privilege escalation attempts. Additionally, encrypting sensitive data, enforcing access policies, and continuously monitoring audit logs helps strengthen defenses.
AI Attack Lifecycle and AWS Defenses
To better understand this, for example, it helps to visualize AWS service that defends against AI-powered cyberattacks across the attack lifecycle.
|
Stage |
AI Threat Example |
AWS Service Mitigation |
|
Stage 1: Reconnaissance |
Automated scanning of cloud resources |
GuardDuty, Macie, Security Hub |
|
Stage 2: Initial Access |
AI-generated phishing or deepfake login attempts |
GuardDuty, Security Hub |
|
Stage 3: Execution |
Malware deployment, container compromise |
Inspector, Shield Advanced, WAF |
|
Stage 4: Persistence & Lateral Move |
Exploit misconfigurations, escalate privileges |
IAM anomaly detection, Config rules |
|
Stage 5: Exfiltration |
Sensitive data extraction |
Macie, KMS encryption, CloudTrail monitoring |
|
Stage 6: Impact |
Disruption, fraud, data breach |
Security Hub alerts, automated Lambda remediation |
AWS Services for Mitigating AI-Powered Cyberattacks
AWS provides AI-driven security services that combine automation, machine learning, and cloud-scale visibility to secure workloads effectively.
- Amazon GuardDuty – Intelligent Threat Detection
- Uses machine learning and anomaly detection to identify unusual API calls, network traffic, or account activity.
- Use Case: Detecting rapid automated login attempts from multiple geolocations (possible AI bot attack).
- Works seamlessly with AWS Organizations for multi-account monitoring.
- AWS Security Hub – Centralized Security Management
- Aggregates findings from GuardDuty, Macie, Inspector, and partner solutions.
- Uses AI to prioritize high-risk alerts and reduce noise for security teams.
- Proactive Defense: Automate remediation workflows using AWS Lambda, e.g., disabling compromised credentials instantly.
- Amazon Macie – Protect Sensitive Data
- AI-driven discovery and classification of personally identifiable information (PII) and sensitive information in S3.
- Monitors unusual access patterns to detect potential AI-driven exfiltration attempts.
- Supports encryption at rest and in transit, plus compliance audits (GDPR, HIPAA, CCPA).
- AWS WAF & AWS Shield Advanced – Web and DDoS Protection
- AWS WAF identifies abnormal request patterns from bots or AI-powered scraping using machine learning.
- Shield Advanced provides AI-driven DDoS mitigation at the network and application layers.
- Protects public-facing applications from automated AI attacks.
- AWS Security Agent – Continuous Application Security
- Embeds security into CI/CD pipelines for automated design reviews, code analysis, and penetration testing.
- Additionally, it detects vulnerabilities before deployment, preventing AI-assisted attacks on applications and APIs.
- Supports integration with SageMaker, Lambda, and containerized workloads for holistic security coverage.
- Amazon Detective – Investigative Analytics
- Uses machine learning to map relationships between resources, users, and activities.
- Uncovers the origin of sophisticated AI attacks and visualizes attack paths.
- AWS Identity and Access Management (IAM) with AI Policies
- Enforces least-privilege access and anomaly detection on credentials.
- Detects unusual patterns that may indicate automated AI attempts to escalate privileges.
AI Security in CI/CD Pipelines
Modern software pipelines are a key target for AI-powered attacks, as attackers can inject malicious code, compromise ML models, or exfiltrate secrets. Consequently, AWS enables secure CI/CD for ML and software applications. First, organizations should integrate security checks early using AWS Security Agent and Amazon Inspector to detect vulnerabilities during the build phase. Next, validating ML model inputs with SageMaker Model Monitor helps catch anomalies or adversarial inputs before deployment. Moreover, automating remediation through Security Hub by triggering Lambda scripts can quarantine compromised builds or revoke credentials. Finally, enforcing governance with AWS Config ensures that CI/CD pipelines comply with organizational security policies and prevents misconfigurations.
Best Practices for Organizations
For example, organizations should enable continuous monitoring with GuardDuty, Macie, and Security Hub, which provide AI-driven, real-time insights. In addition, automating responses using Lambda ensures instant mitigation of threats detected by AI. Moreover, encrypting sensitive data, rotating keys, and monitoring access with Macie and IAM helps secure critical information. Similarly, validating ML workload inputs, monitoring outputs, and auditing model drift strengthens machine learning defenses. Furthermore, implementing a zero-trust architecture with strict access controls and network segmentation reduces exposure to attacks. Finally, regular audits and assessments using Inspector, Config, and Security Hub support compliance and identify vulnerabilities proactively.
Emerging Threats and Future Outlook
Currently, AI attacks are becoming more sophisticated and automated, particularly targeting cloud environments and machine learning models. Meanwhile, cloud-native AI defenses are evolving, including predictive threat intelligence, adaptive ML-driven defenses, and autonomous response systems. Therefore, security teams need AI literacy to effectively leverage AWS services and counter AI-powered threats.
Conclusion
In conclusion, AI is both a powerful tool and a potent weapon in the wrong hands. Therefore, organizations must adopt AI-powered security solutions to stay ahead as attackers harness AI to scale attacks. Ultimately, AWS provides a holistic, AI-driven security ecosystem from GuardDuty and Macie to Security Agent and WAF, helping organizations detect threats, protect sensitive data, secure CI/CD pipelines, and respond rapidly to AI-powered cyberattacks. By combining automation, machine learning, and continuous monitoring, organizations can maintain trust, protect critical workloads, and defend against the next generation of cyber threats.
References:
- AWS Security Services
- Amazon GuardDuty
- AWS Security Hub
- Amazon Macie
- AWS Security Agent
- AWS WAF & Shield
- Amazon Detective


















