Last updated on December 26, 2025
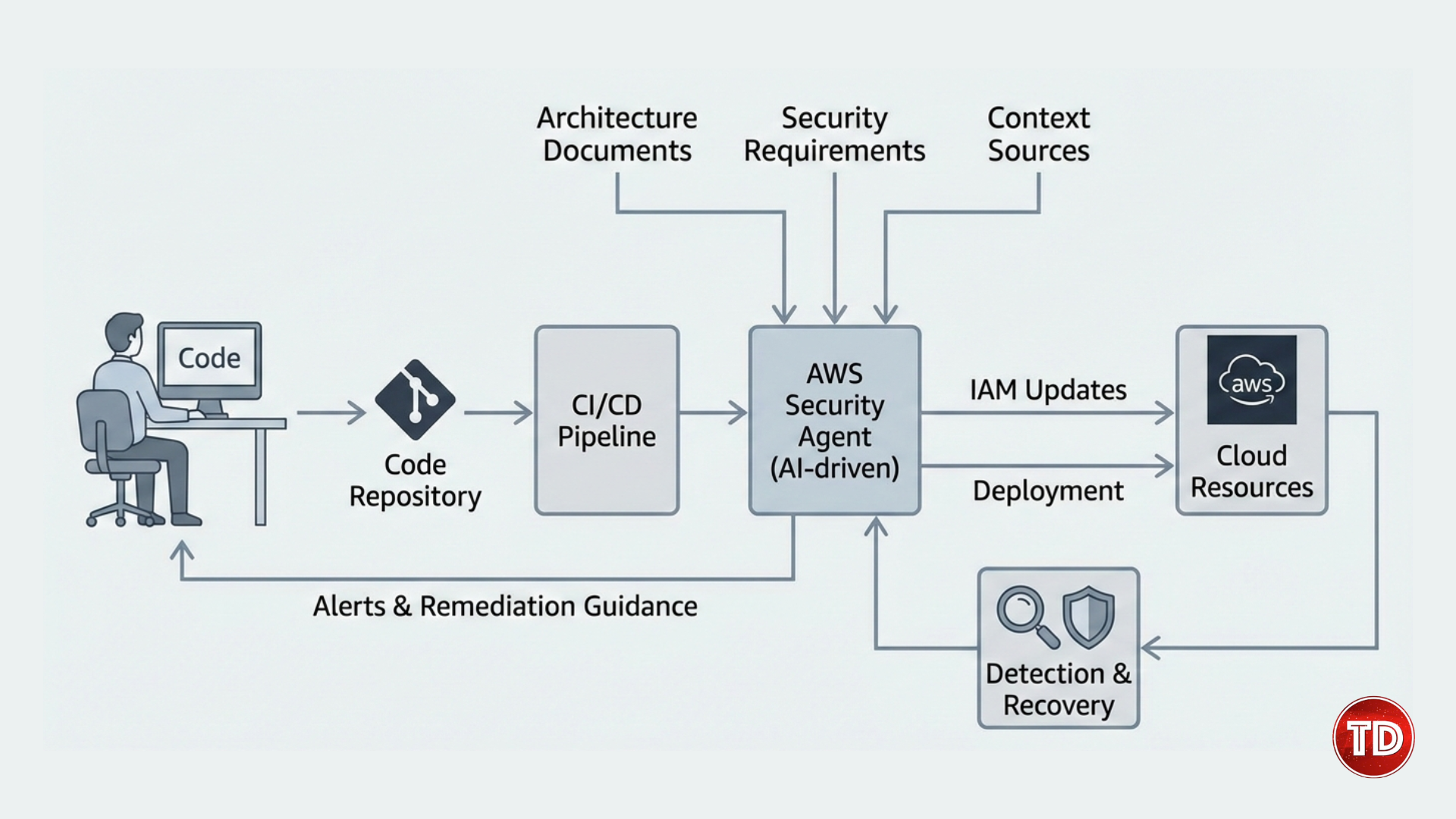
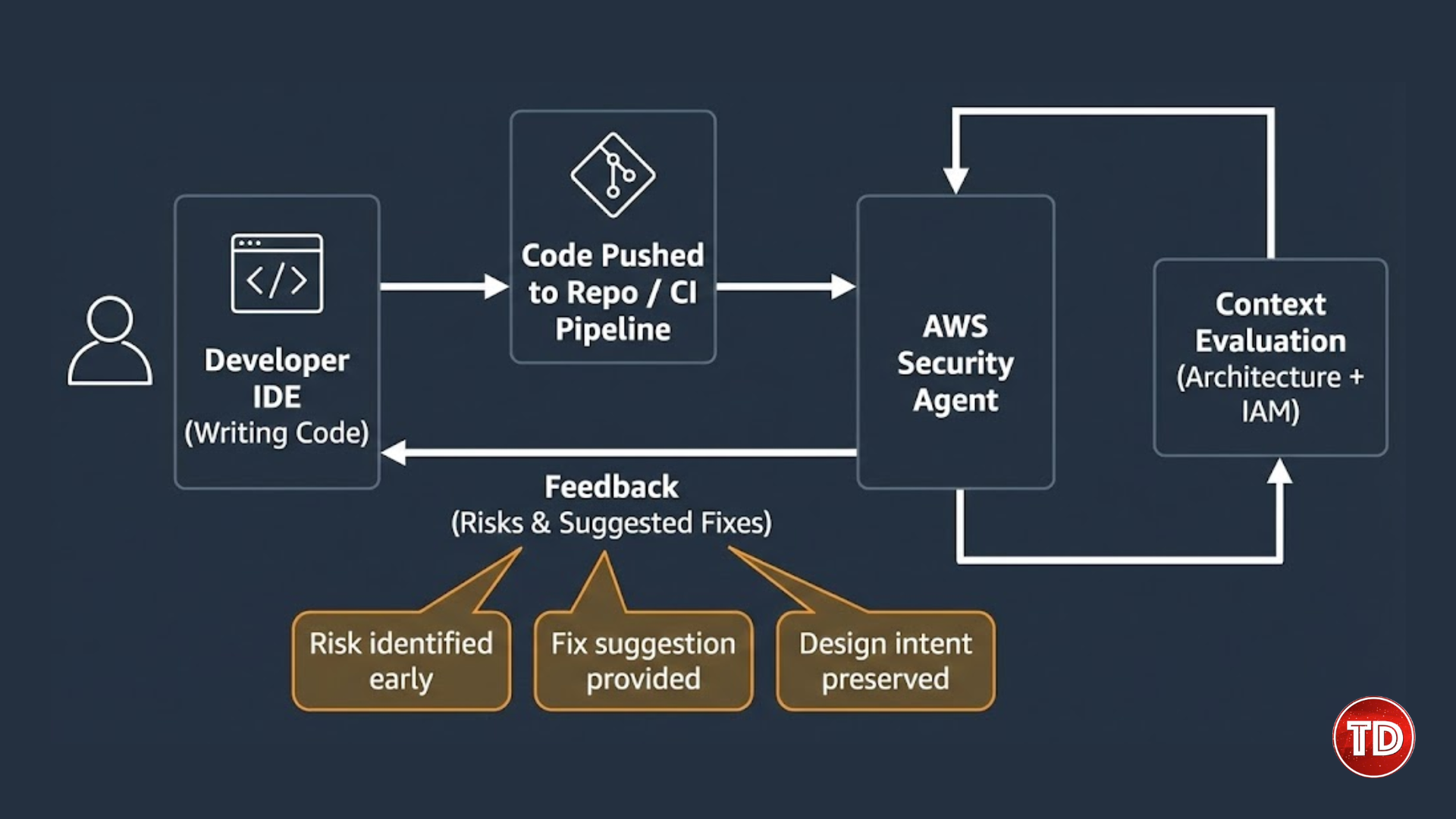
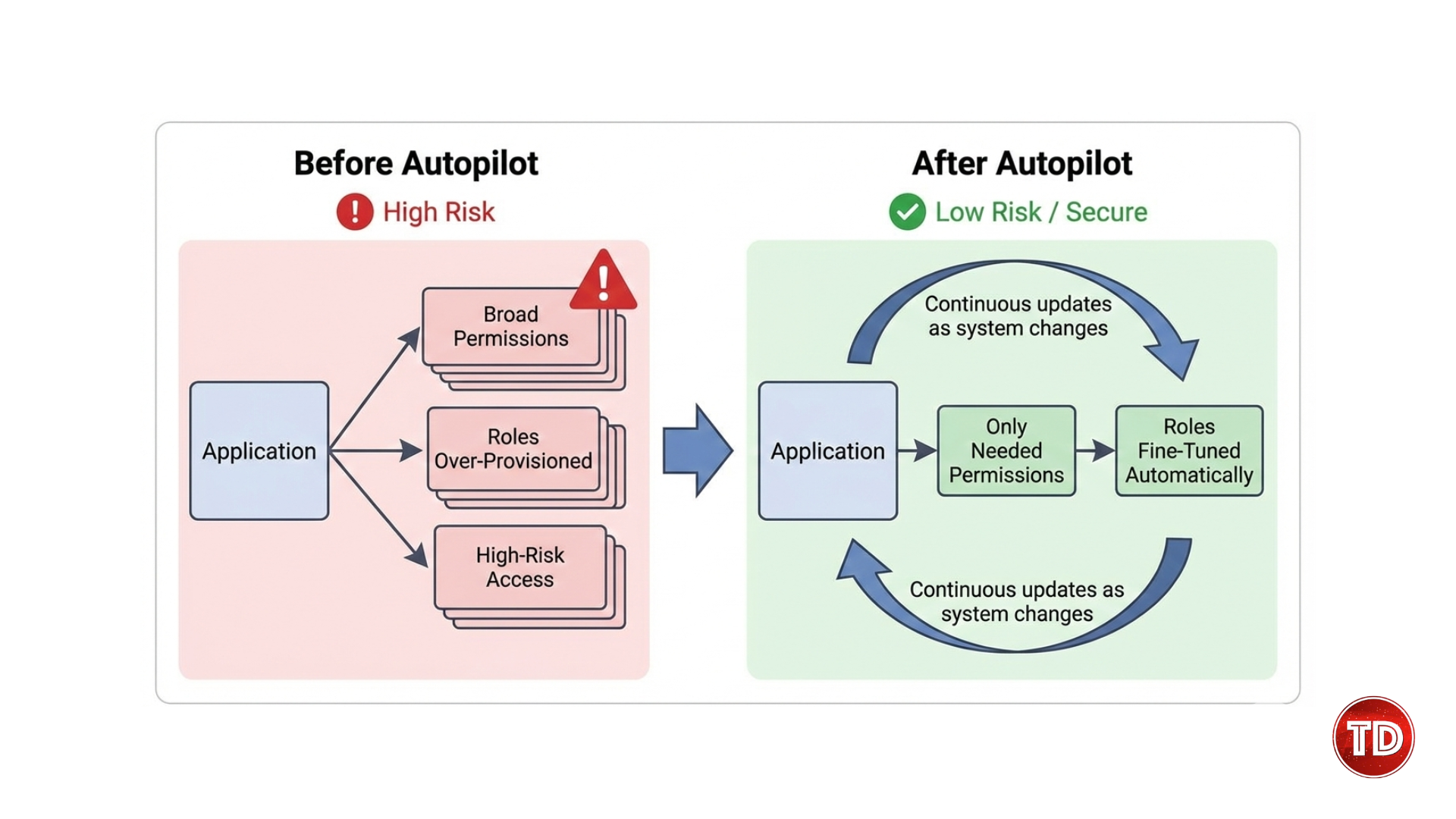
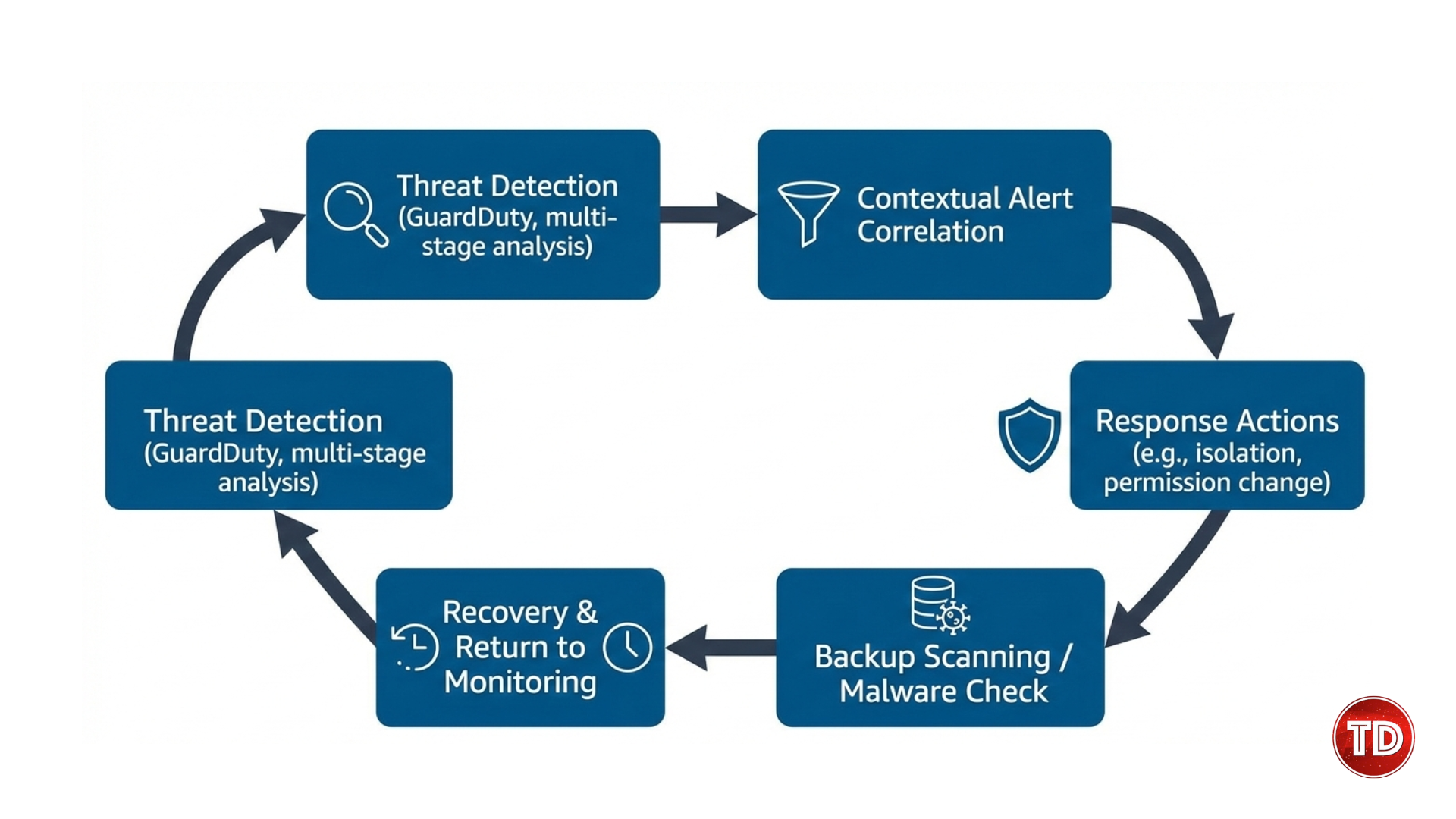
Cloud computing continues to accelerate at a pace that traditional security models were never designed to support. Development teams now provision infrastructure in minutes, deploy services continuously, and scale applications automatically. However, security processes often lag behind this speed. In many organizations, security still enters the workflow after key architectural decisions are already finalized. As a result, teams spend more time fixing problems than preventing them. Although many organizations attempt to shift security earlier in development, the results are often disappointing. Security tools may run during build or deployment stages, yet they frequently lack the context required to provide meaningful guidance. Alerts become repetitive, findings lack prioritization, and security teams remain reactive. Developers, in turn, begin to see security as a source of friction rather than a collaborative partner. This growing disconnect highlights the need for a new approach. Security must evolve to match the speed and complexity of modern cloud systems. At AWS re Invent 2025, AWS introduced a significant shift in cloud security strategy by focusing on AI driven cloud security. Instead of adding more scanners or rules, AWS presented intelligent agents that reason about systems, understand intent, and operate continuously throughout the software lifecycle. The concept of shifting security left is widely adopted across the industry. Teams scan code earlier, validate infrastructure templates, and review configurations before deployment. Despite these efforts, vulnerabilities still surface in production environments. This outcome suggests that the issue is not a lack of tooling but a lack of effectiveness. Traditional security tools are primarily pattern based. They look for known misconfigurations, insecure defaults, or vulnerable dependencies. While these checks are valuable, they do not account for how components interact within a system. As a result, they fail to identify risks that emerge from architecture design or service relationships. Modern cloud environments are inherently distributed. Applications rely on managed services, asynchronous communication, and dynamic identity permissions. Security risks often arise at trust boundaries, during data movement, or through unintended service interactions. Isolated tools that analyze components independently cannot reason about these complex relationships. Moving the same tools earlier in the pipeline does not solve this problem. Instead, it introduces incomplete findings sooner without providing clarity. Therefore, organizations require security solutions that understand systems holistically and adapt continuously as environments evolve. Figure 1. AI-driven cloud security architecture using AWS agentic security AI driven cloud security addresses these challenges by combining continuous analysis with contextual understanding. Rather than relying on static rules, AI driven systems evaluate architecture, identity, data flows, and runtime behavior together. This holistic approach enables security insights that are both accurate and actionable. At AWS re Invent 2025, AWS demonstrated how intelligent agents can reason about cloud environments across the entire lifecycle. These agents do not simply detect issues after deployment. Instead, they understand system intent and assess how changes affect overall security posture. Because of this continuous reasoning, security becomes proactive rather than reactive. Risks are identified during design and implementation when fixes are easier and less costly. Developers receive guidance in real time, which encourages collaboration rather than resistance. Over time, this approach leads to more secure systems and faster delivery cycles. One of the most impactful announcements was the AWS Security Agent, currently available in preview. Unlike traditional scanners, the AWS Security Agent functions as an ongoing development partner rather than a checkpoint tool. The agent ingests context from multiple sources. These include architecture diagrams, infrastructure templates, security requirements, and application code. By understanding what the system is intended to do, the agent can evaluate changes with far greater accuracy. When developers modify infrastructure or application logic, the agent analyzes those changes in context. Instead of producing long reports after builds complete, it provides feedback during development. This timing is critical because fixes are simpler when applied early. Furthermore, the agent explains why a change introduces risk and how it could be exploited. This educational aspect helps developers build stronger security intuition over time. As a result, security becomes integrated into daily workflows rather than treated as an external requirement. Figure 2. AI-driven cloud security integrated into the development workflow Traditional security tools operate at fixed points in time. They analyze snapshots of systems and generate findings based on that moment. Unfortunately, cloud systems evolve continuously, which quickly renders these snapshots outdated. The AWS Security Agent applies continuous reasoning. Each change is evaluated in relation to the entire system, including services, identity permissions, and data flows. When the agent detects a risky pattern, it assesses potential impact rather than flagging isolated issues. For example, a minor permission change might appear harmless on its own. However, when combined with existing access paths, it could enable privilege escalation. The agent identifies these chained risks by reasoning across the system. Over time, this approach reduces alert fatigue. Developers receive fewer but more relevant findings. Security teams gain confidence that alerts represent meaningful risks rather than noise. Consequently, remediation becomes faster and more effective. Security testing has traditionally been slow and infrequent. Penetration tests are often scheduled months in advance and scoped based on static assumptions. By the time testing concludes, systems may have already changed. Agent based security introduces adaptive testing. The AWS Security Agent generates attack paths based on architecture and runtime behavior. As systems evolve, these attack paths update automatically. This adaptive approach identifies chained vulnerabilities that static tools often miss. For example, a combination of misconfigured identity permissions and network exposure may enable lateral movement. Traditional scanners might flag each issue separately without identifying the combined risk. By detecting these scenarios early, teams can address root causes before deployment. This strengthens AI driven cloud security by aligning testing with real world attacker behavior. Figure 3. AI-driven cloud security enforcing least-privilege IAM policies Identity remains one of the most critical and challenging aspects of cloud security. In fast moving environments, teams often grant broad permissions to unblock development. Over time, these permissions accumulate and increase exposure. Manual identity management does not scale well. Reviewing policies across dozens or hundreds of services quickly becomes impractical. Even experienced teams struggle to maintain least privilege consistently. Recognizing this challenge, AWS introduced IAM Policy Autopilot at re Invent 2025. This feature uses intent based access to generate and maintain policies automatically. IAM Policy Autopilot creates policies based on actual usage rather than assumptions. It observes how applications interact with AWS services and generates permissions that match real needs. Importantly, these policies evolve over time. When applications add new features, permissions adjust automatically. When features are removed, unnecessary permissions are eliminated. Least privilege becomes a continuous state rather than a one time effort. This automation significantly reduces risk while supporting rapid development. Teams no longer need to choose between speed and security. Instead, identity adapts as systems change. Automation itself introduces new security considerations. Agents that modify policies or infrastructure must operate safely to avoid becoming attack vectors. AWS addressed this by enforcing strict identity boundaries for automation components. Agents operate with scoped permissions and are monitored continuously. This ensures that automation strengthens security rather than undermining it. By securing the automation layer, AWS reinforces trust in AI driven cloud security mechanisms. Even the most advanced preventive controls cannot eliminate all threats. Therefore, detection and response remain essential components of cloud security. Traditional detection tools often generate large volumes of isolated alerts. Security teams must manually correlate events across services to understand attacker behavior. This process is time consuming and error prone. AWS enhanced threat detection by correlating signals across compute, identity, and network layers. By connecting these signals, teams gain visibility into multi step attacks rather than isolated events. For example, suspicious identity activity combined with unusual network behavior may indicate compromise. Contextual detection surfaces these patterns clearly, enabling faster response. Figure 4 AI driven cloud security detection response and secure recovery workflow Recovery systems are often overlooked in security planning. However, attackers increasingly target backups to ensure persistence. At re Invent 2025, AWS introduced malware scanning for backups. This capability ensures that restored systems are clean and reduces the risk of reinfection. By securing recovery processes, AWS strengthens overall resilience. Teams can restore services with greater confidence and reduce downtime during incidents. Together, these benefits transform security into a foundational capability that supports rapid and reliable cloud delivery. AWS re Invent 2025 marks a significant evolution in cloud security. By introducing agent based intelligence across development, identity, detection, and recovery, AWS aligns security with how modern systems are built. AI driven cloud security moves organizations beyond reactive defenses. Instead, it embeds prevention into every stage of the lifecycle. As cloud environments continue to grow in complexity, this approach provides a scalable and sustainable path forward.
Why Traditional Shift-Left Security Falls Short
Why AI Driven Cloud Security Is Different
AWS Security Agent as a Continuous Development Partner
Continuous and Adaptive Security During Development
Adaptive Security Testing During Development
Identity as the Foundation of Cloud Security
How IAM Policy Autopilot Works
Securing the Automation Layer
Improving Detection with Contextual Intelligence
Strengthening Recovery and Resilience
REFERENCES
🚀 Get 20% OFF All Azure Products Today — Azure Super Sale!
Learn AWS with our PlayCloud Hands-On Labs
$2.99 AWS and Azure Exam Study Guide eBooks
New AWS Generative AI Developer Professional Course AIP-C01
Learn GCP By Doing! Try Our GCP PlayCloud
Learn Azure with our Azure PlayCloud
FREE AI and AWS Digital Courses
FREE AWS, Azure, GCP Practice Test Samplers
Subscribe to our YouTube Channel
Follow Us On Linkedin